Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store

Quash EDR/XDR Exploits With These Countermeasures

Cyble — Analysis - SharkBot Malware v1.63

Appdome How to Use Appdome MOBILEBot™ Defense
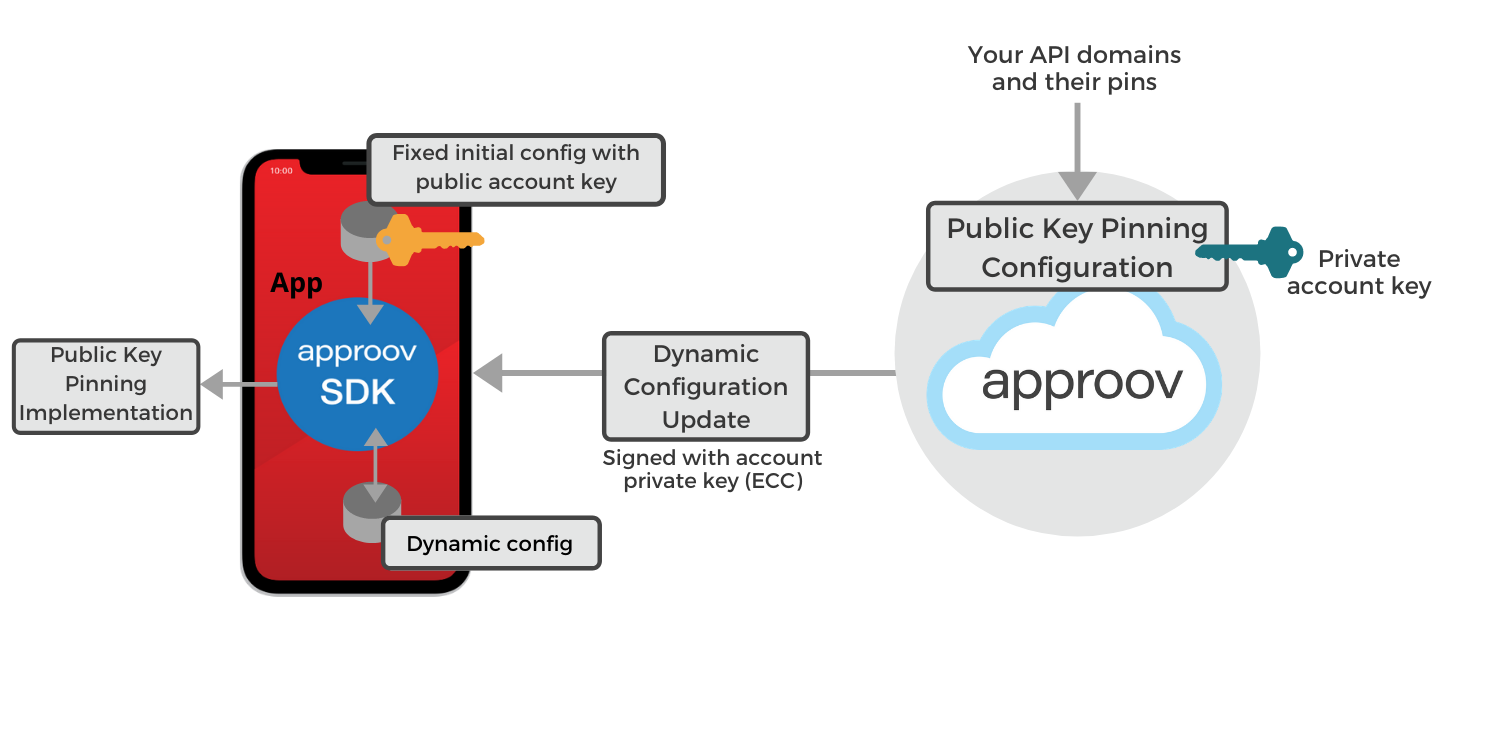
How to Protect Against Certificate Pinning Bypassing

Android: With Android 14, Google has a new plan to make your

Android App Disguised as a QR scanner, Spreads Joker Variant Trojan
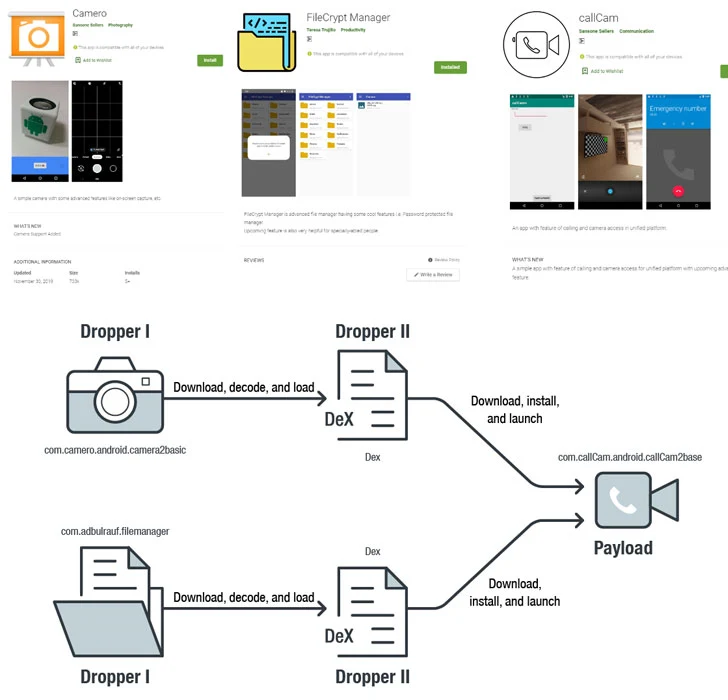
3 Google Play Store Apps Exploit Android Zero-Day Used by NSO Group

Analysis of dynamic code updating in Android with security

DLLSpy – Tighten Your Defense by Discovering DLL Hijacking Easily

What Is Rootkit?

Attackers use dynamic code loading to bypass Google Play store's

Attackers uses repackaging to publish forged applications on
de
por adulto (o preço varia de acordo com o tamanho do grupo)






