Towards an Automated Process to Categorise Tor's Hidden Services
Por um escritor misterioso
Descrição
Egregor ransomware: Maze's heir apparent – Sophos News

Journal of Automation, Mobile Robotics and Intelligent Systems, vol. 16, no. 4 (2022) by Ł-PIAP - Issuu

The 6 Most Secure Email Services and the Security Measures They Practice
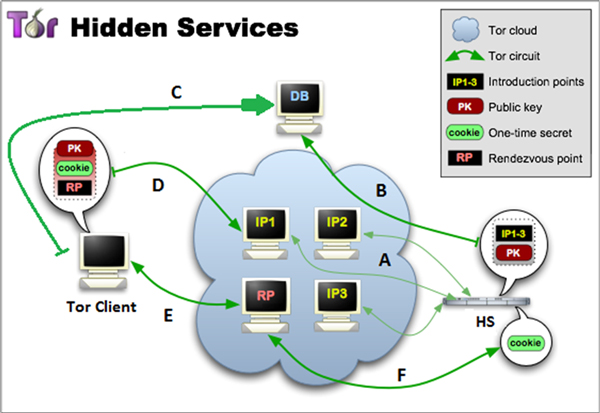
Tor Hidden Services - Infodrug

FlowMFD: Characterisation and classification of tor traffic using MFD chromatographic features and spatial–temporal modelling - He - 2023 - IET Information Security - Wiley Online Library

How Our New Anti-Bot AI Prevents Millions of Brute-Force Attacks - SiteGround Blog

Are TOR Hidden Services really hidden? Demystifying HS Directory surveillance by injecting Decoys inside TOR!

Exploring the surface, deep and dark web: unveiling hidden insights

TOR Fronting — Utilising Hidden Services to Hide Attack Infrastructure, by Vincent Yiu
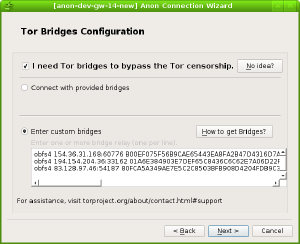
Configure (Private) (Obfuscated) Tor Bridges

The Dark web - Why the hidden part of the web is even more dangerous?
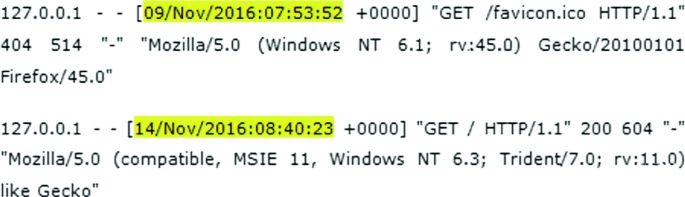
Towards an Automated Process to Categorise Tor's Hidden Services

TOR Fronting — Utilising Hidden Services to Hide Attack Infrastructure, by Vincent Yiu

Normal use of hidden services and rendezvous servers

Botnet - Wikipedia
de
por adulto (o preço varia de acordo com o tamanho do grupo)