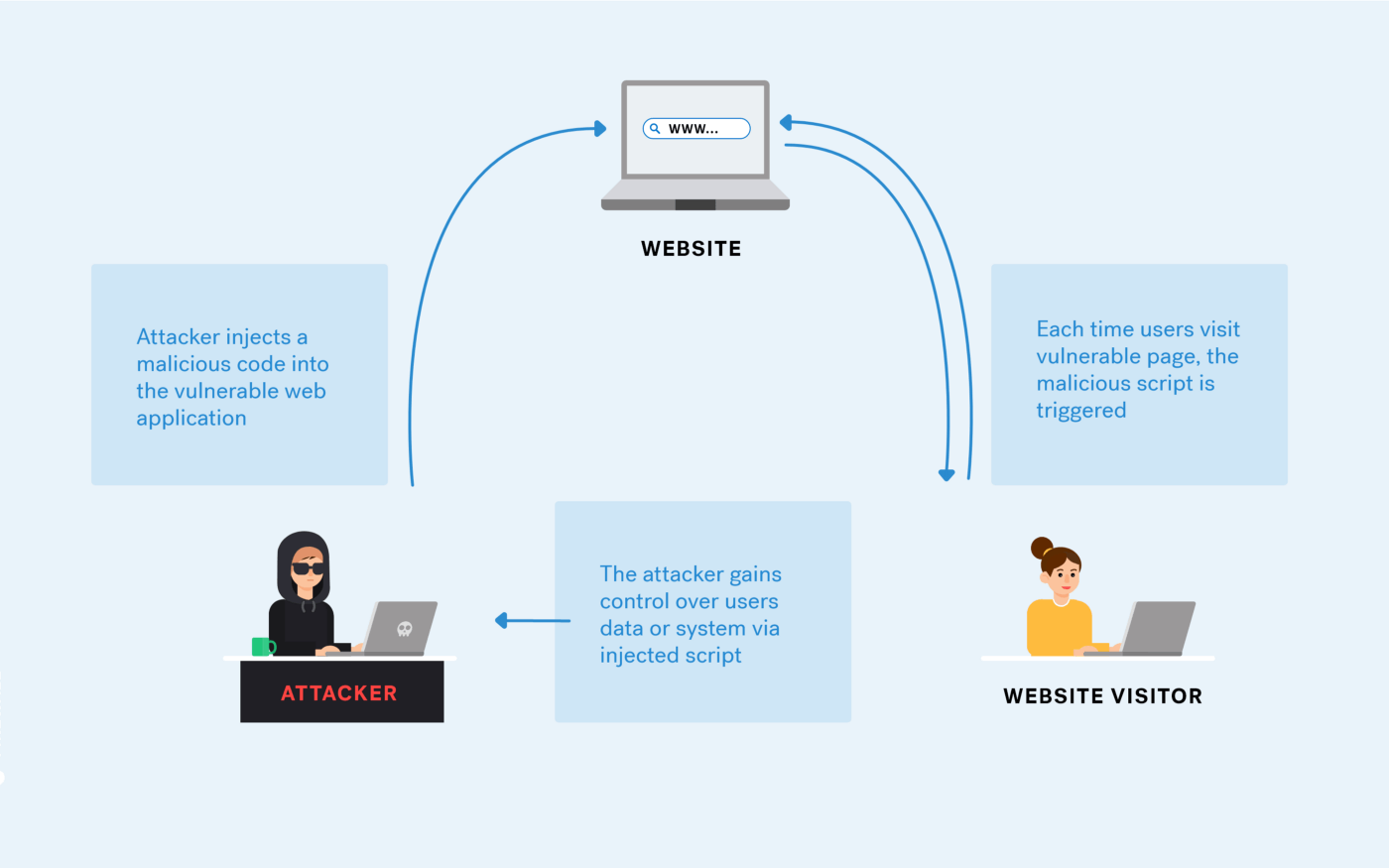
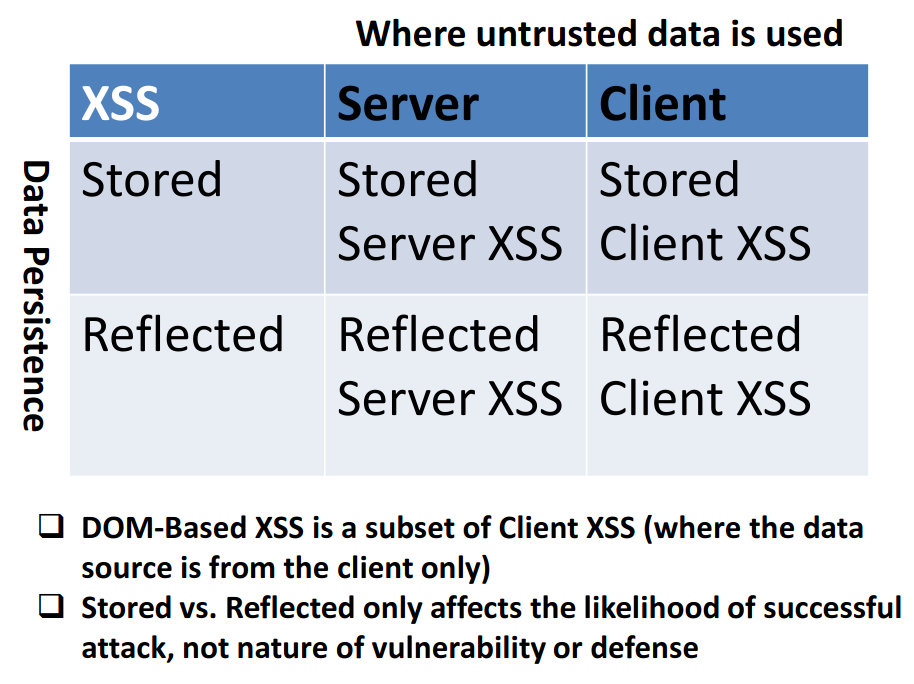
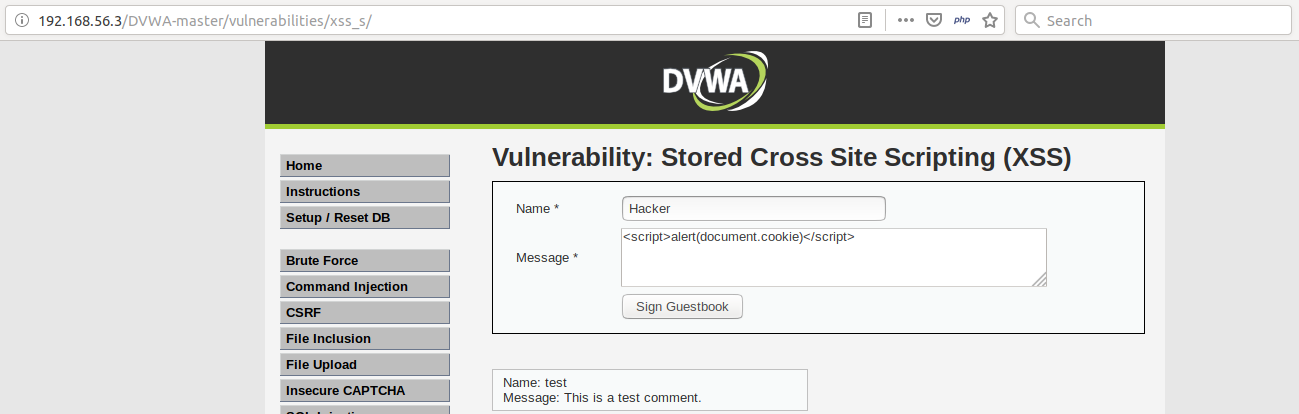
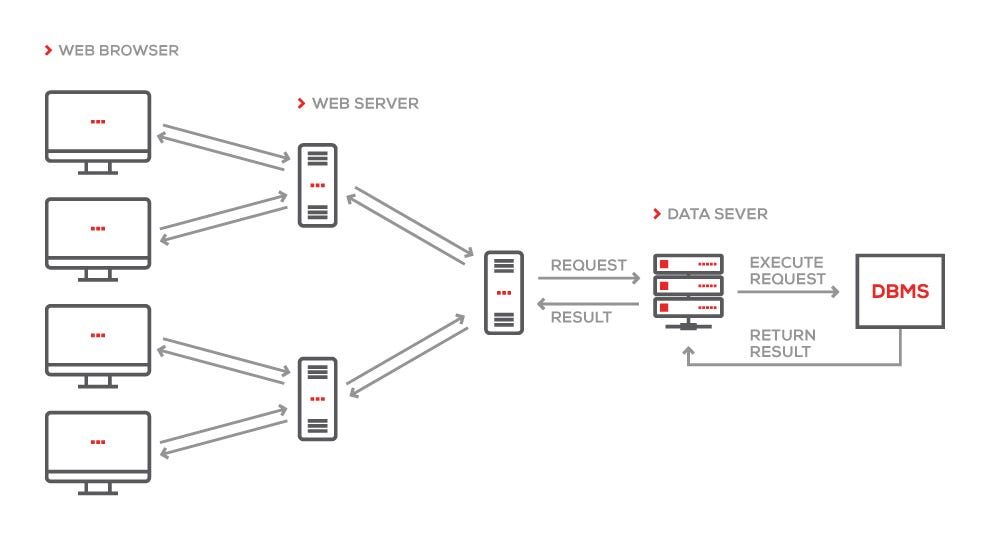
The architecture of XSS attack
Por um escritor misterioso
Descrição

Full article: Case Study: Extenuation of XSS Attacks through Various Detecting and Defending Techniques
Examining Two XSS Vulnerabilities in Azure Services
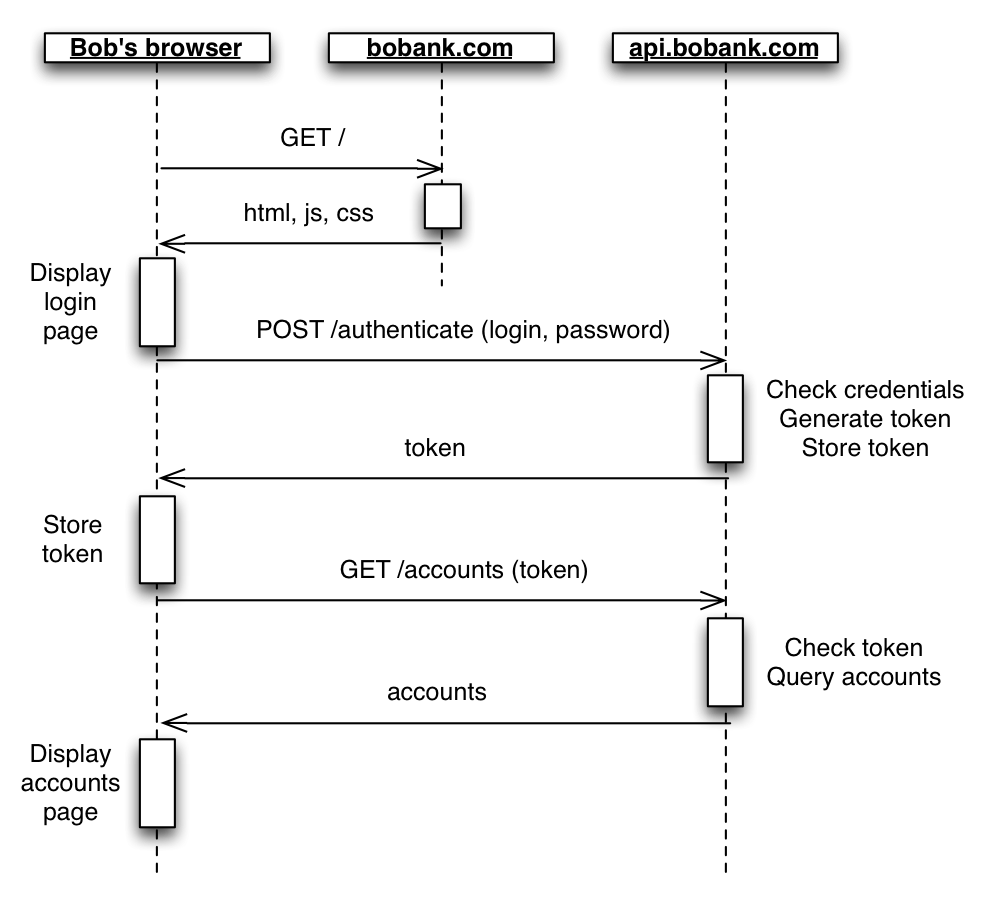
Your API-Centric Web App Is Probably Not Safe Against XSS and CSRF
XSS Explained from Theory to Practice, by Dragan Ilievski

PDF] Figure 1: Architecture of XSS attack Injection of code into un-sanitized parameters, Browser exploitation techniques and Manipulation of application registries which serve as the basis for exploiting and subsequently preventing cross-site

Cross Site Scripting Tutorial, Penetration Testing Tutorial, Web Application Security
The architecture of XSS attack

What is Cross-Site Scripting vulnerability? How to find and prevent an XSS attack? - Studytonight

Cross Site Scripting - How your website is hijacked
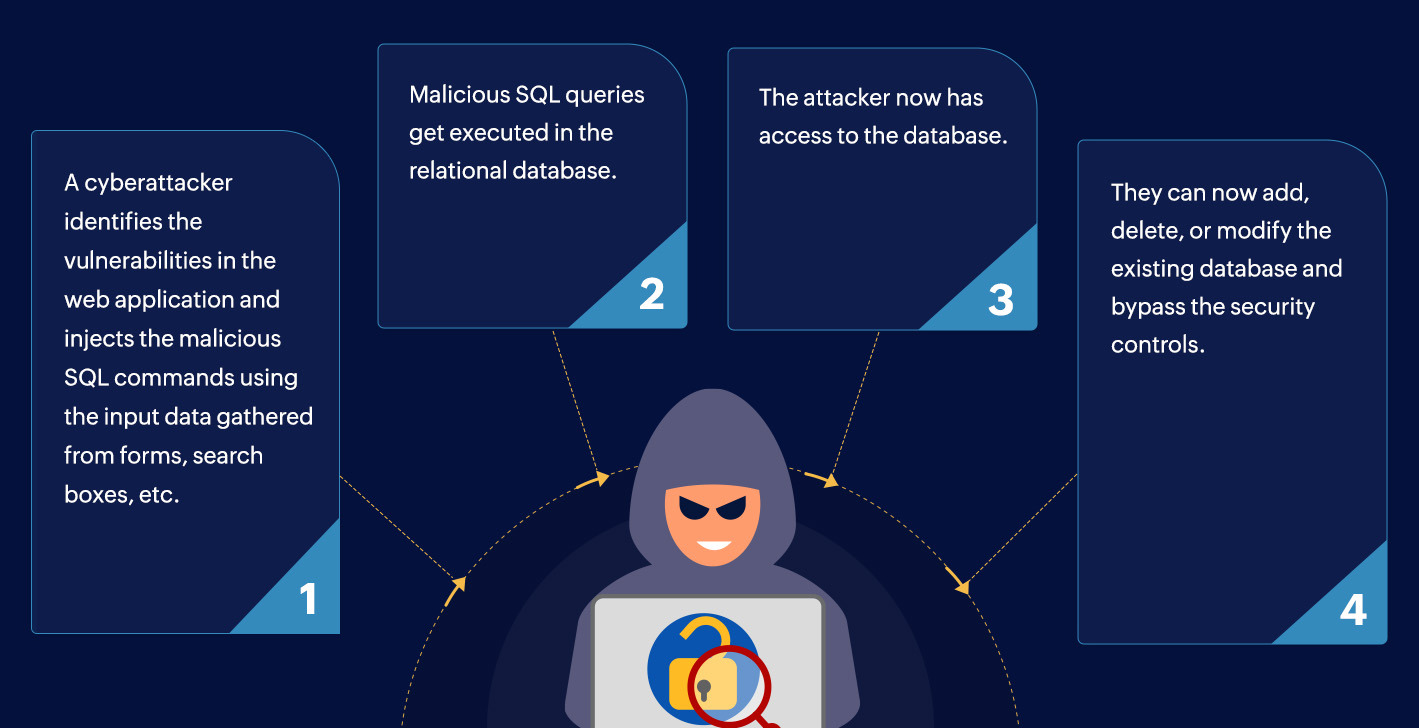
SQL injection and cross-site scripting: The differences and attack anatomy

Prevention Of Cross-Site Scripting Attacks (XSS) On Web Applications In The Client Side
Announcing Sleepy Puppy — Cross-Site Scripting Payload Management for Web Application Security Testing, by Netflix Technology Blog

Stored XSS: Impact, Examples, and Prevention
de
por adulto (o preço varia de acordo com o tamanho do grupo)