Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing
Por um escritor misterioso
Descrição
Welcome to the new age of cyber attacks, where hackers have taken credential stuffing to the next level. Meet Credential Stuffing 2.0, where the use of proxies, CAPTCHA bypassing, CloudFlare security, and GUI tools have become the norm..

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
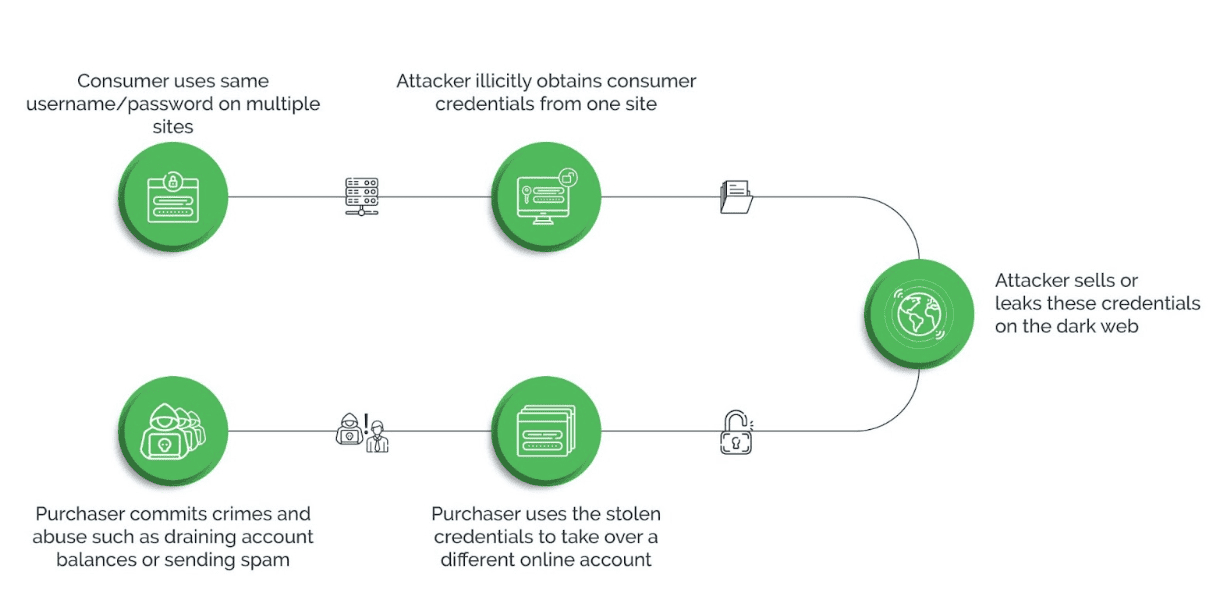
What Is Credential Stuffing?
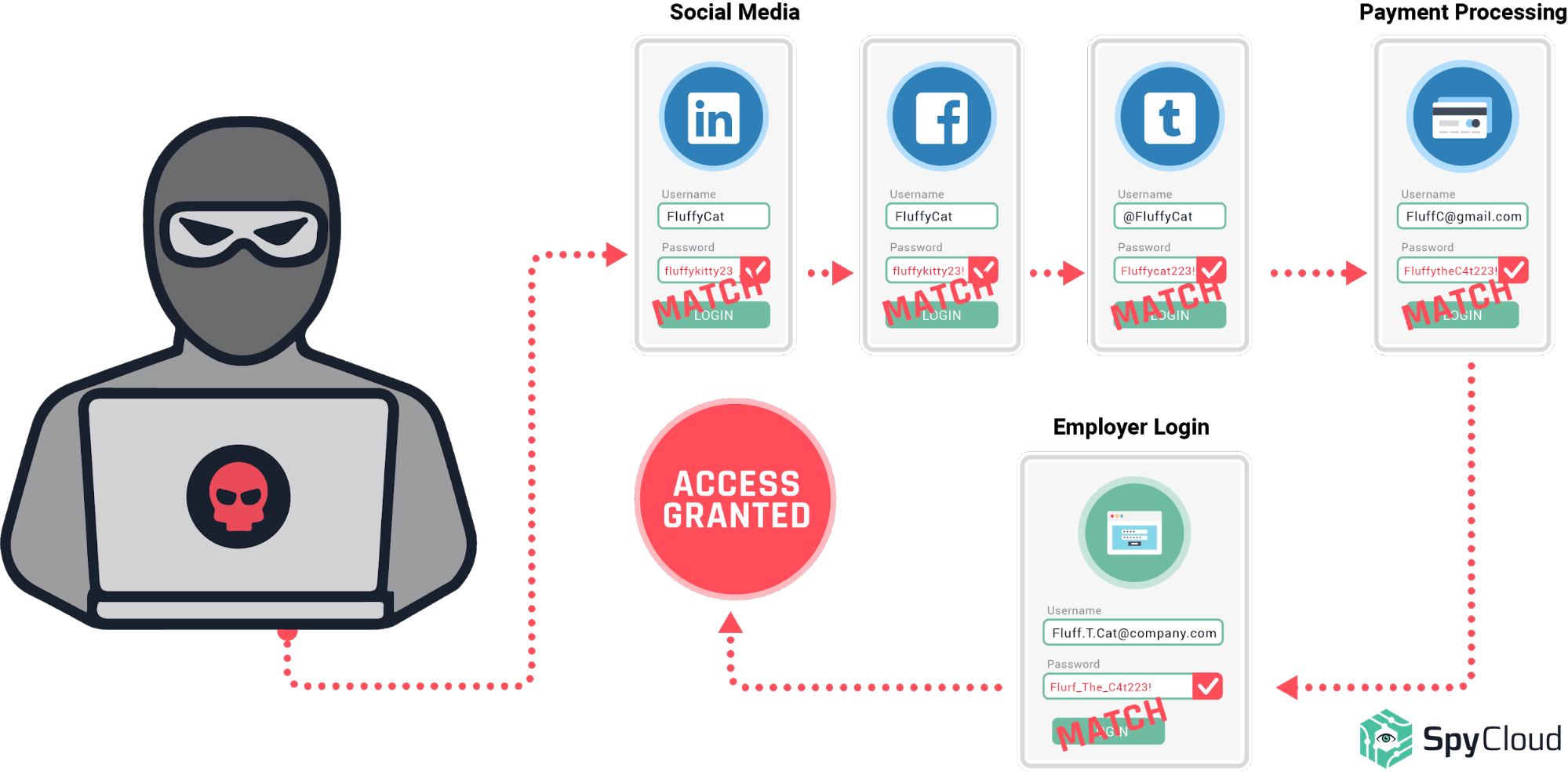
Cracking Tools that Automate Credential Stuffing & ATO

How Credential Stuffing is Evolving - PasswordsCon 2019
How to Prevent Credential Stuffing
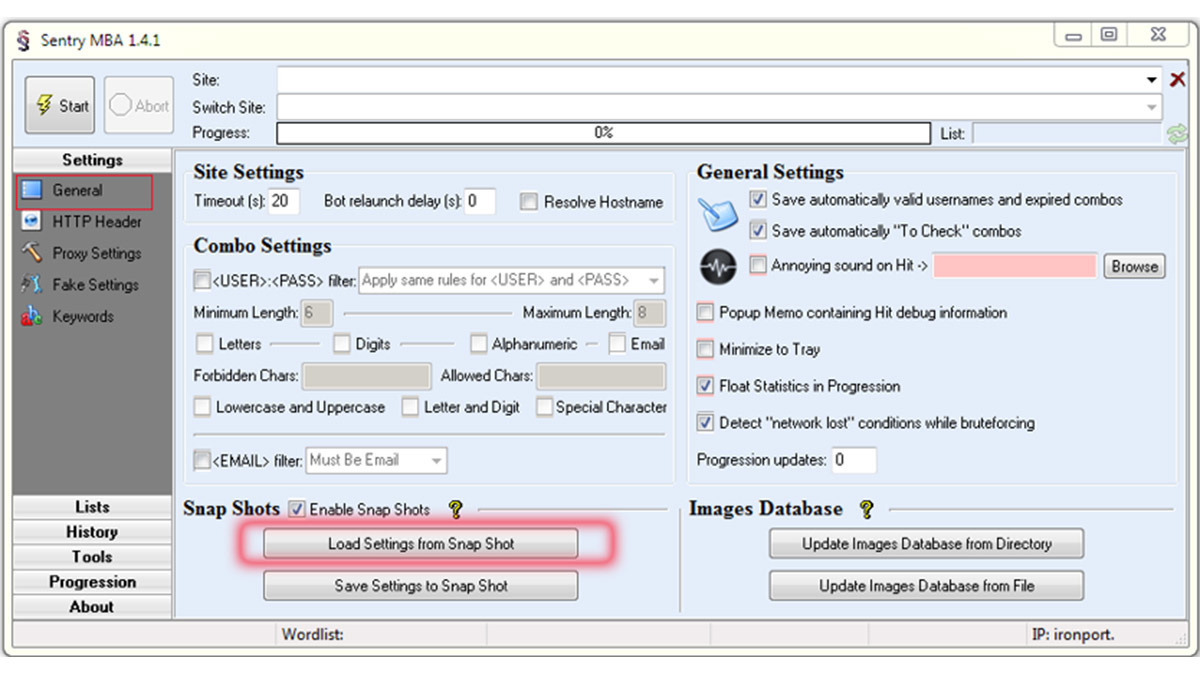
Credential stuffing attacks: How to protect your accounts from being compromised
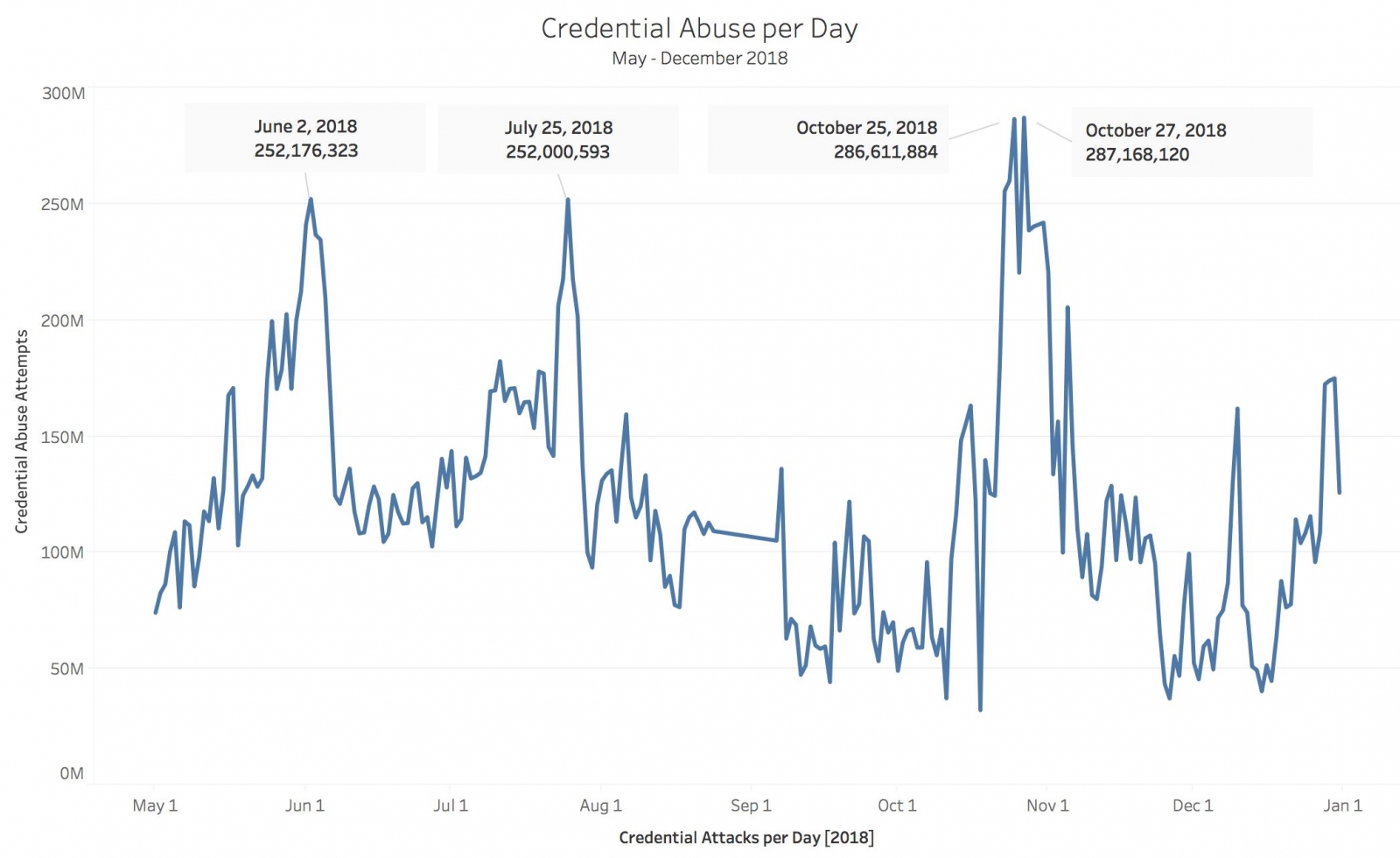
The Anatomy of Highly Profitable Credential Stuffing Attacks
Cracking Tools that Automate Credential Stuffing & ATO
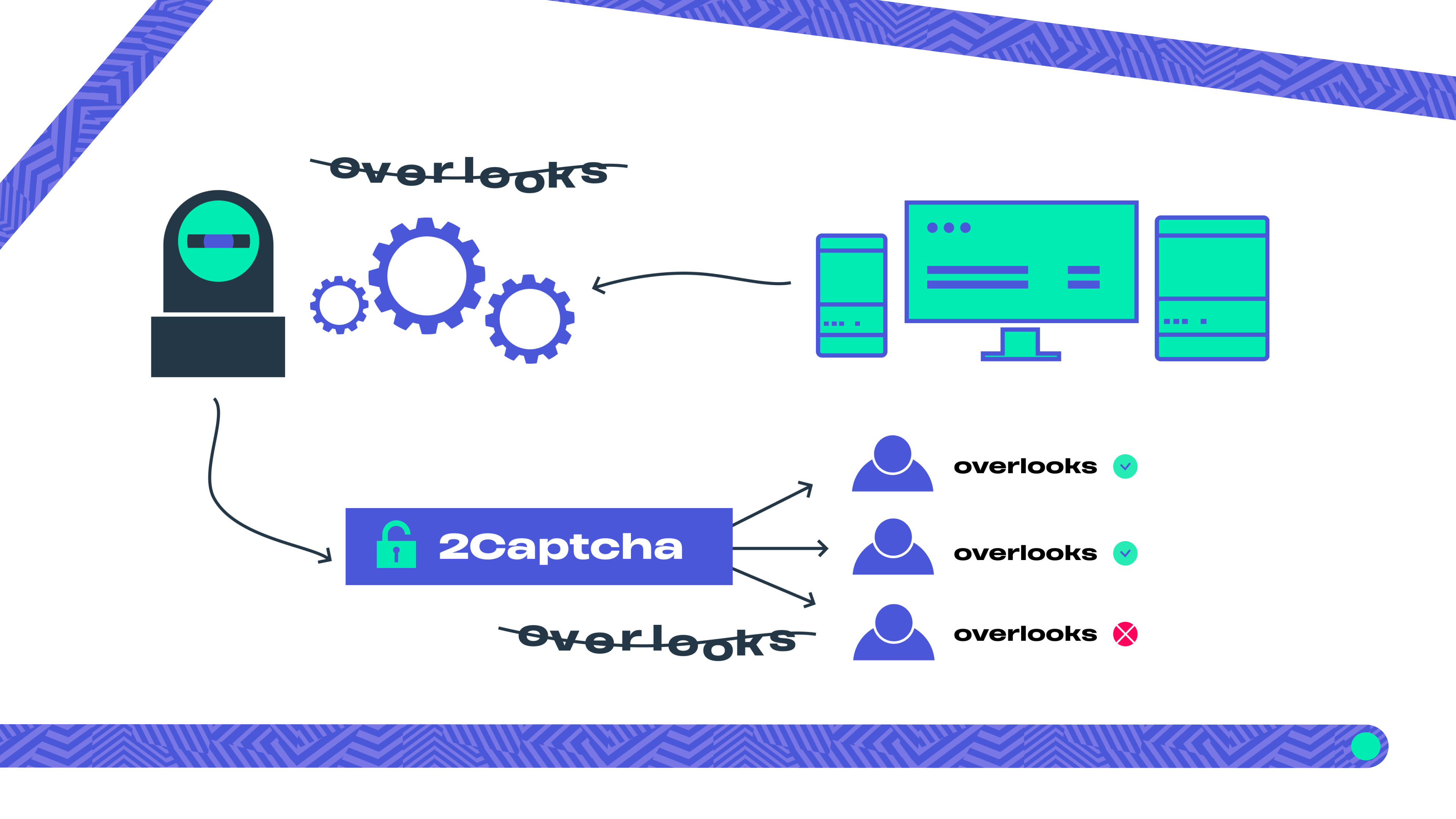
What Are CAPTCHA Proxies and How Do They Work?

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
How to Bypass CAPTCHAs When Web Scraping - Proxyway

Credential Stuffing 2.0: The Use of Proxies, CAPTCHA Bypassing , CloudFlare Security, and GUI Tools
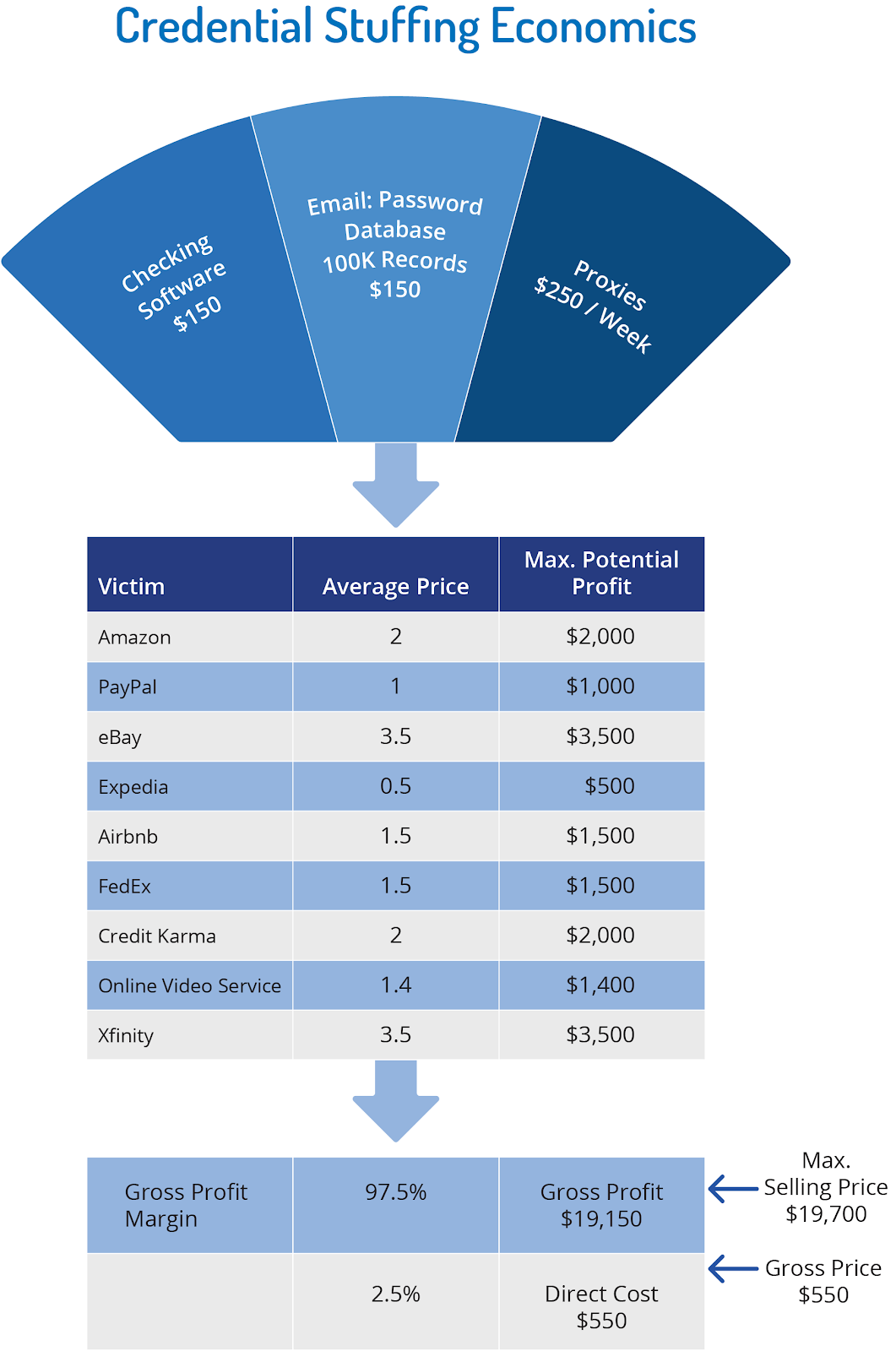
The Anatomy of Highly Profitable Credential Stuffing Attacks
The Economy of Credential Stuffing Attacks
de
por adulto (o preço varia de acordo com o tamanho do grupo)