SSH Passwd, PDF, Cyberwarfare
Por um escritor misterioso
Descrição

EvilProxy Exploits indeed.coms Open Redirect for Microsoft 365 Phishing
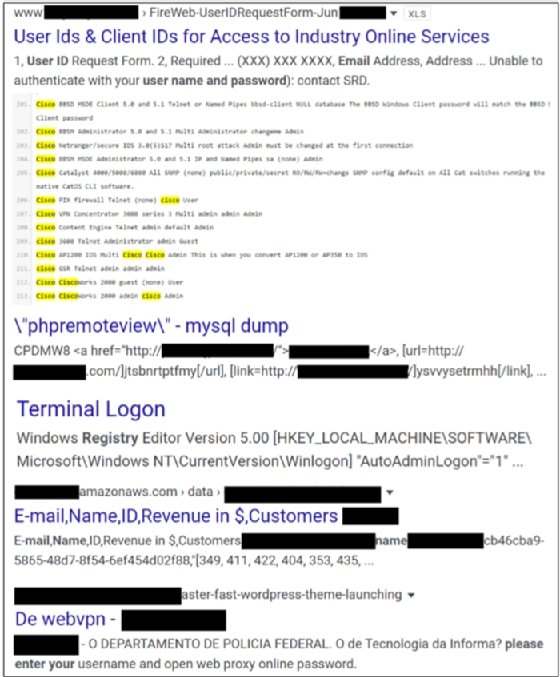
How cyber warfare laws limit risk on a digital battleground

cyber_security_syllabus .pdf, scode network institute
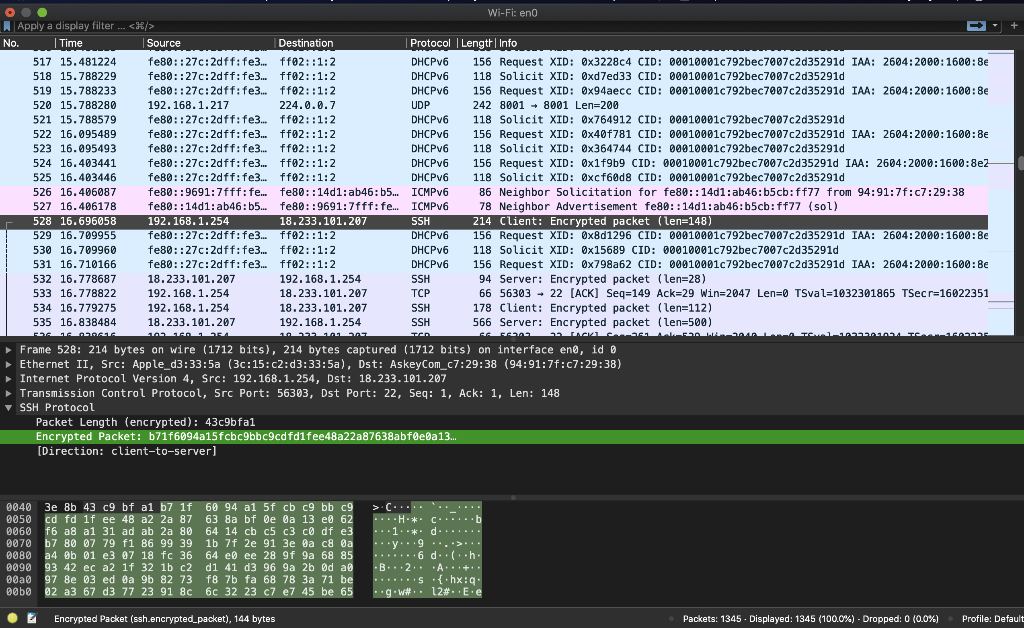
1) Password based authentication: ssh password based

Nitrogen Malware Exploits Google Ads to Deliver Ransomware Attacks

Android Botnet leverages ADB ports and SSH to spread

COVID-19 Cybersecurity Alerts, Coronavirus Phishing Scam, Covid 19 Malware, Cyware
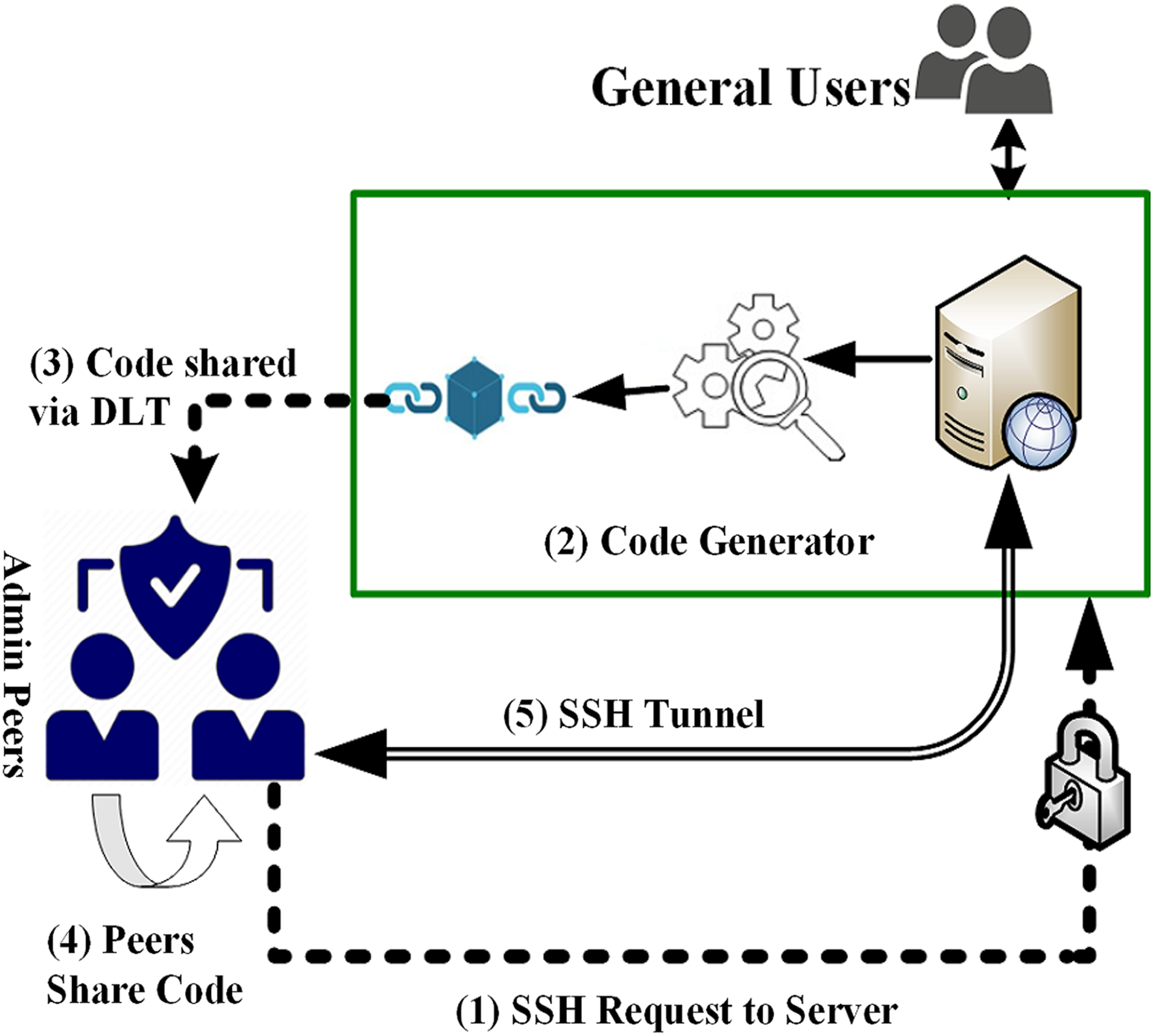
VisTAS: blockchain-based visible and trusted remote authentication system [PeerJ]

Exclusive: A criminal group using SSH TCP direct forward attack is also targeting Italian infrastructure

CyberArk Interview.pdf

Cyber Threats Unveiled: SSH Scanning and XorDDos Propagation

A study on practical uses of common Network protocols

In Other News: Energy Services Firm Hacked, Tech CEO Gets Prison Time, X Glitch Leads to CIA Channel Hijack - SecurityWeek

Android Banking Malware Gigabud RAT Targets Institutions of Various Countries

Cybersecurity and Cyber Warfare: The Ethical Paradox of 'Universal Diffidence
de
por adulto (o preço varia de acordo com o tamanho do grupo)