Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks
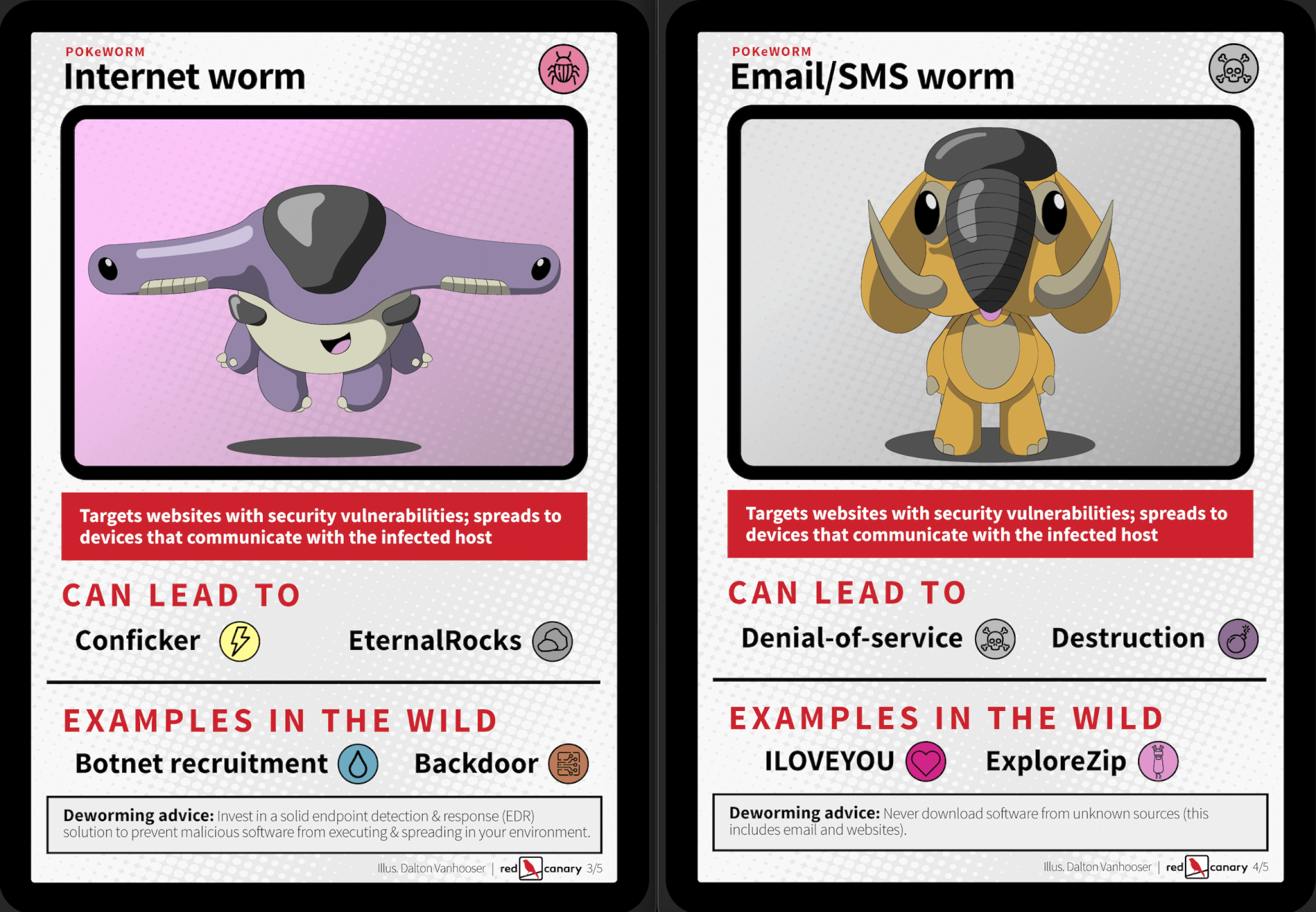
Persistent pests: A taxonomy of computer worms - Red Canary
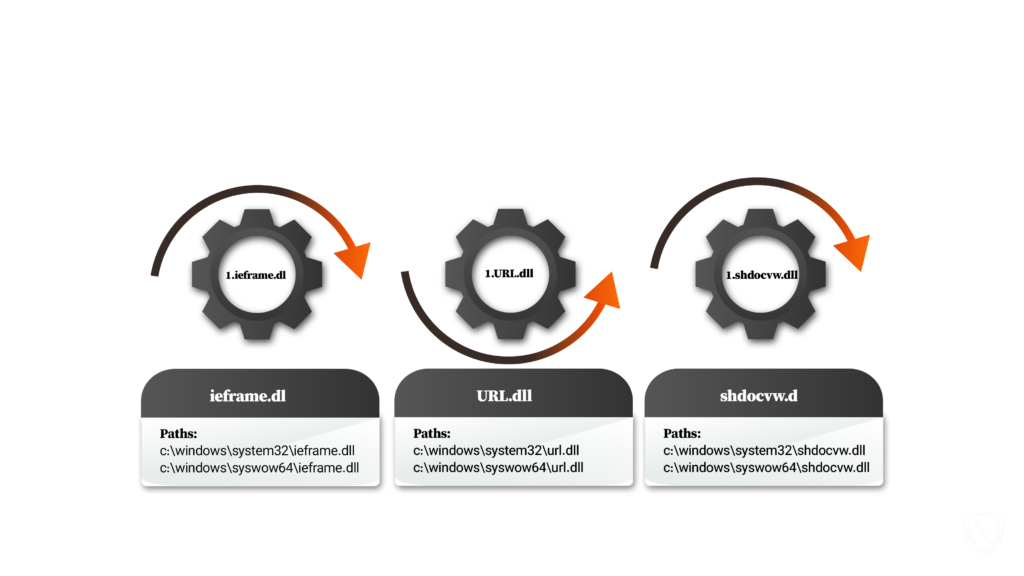
System Binary Proxy Execution Rundll32, Nordic Defender

The Windows Process Journey — rundll32.exe (Windows Host Process), by Shlomi Boutnaru, Ph.D.
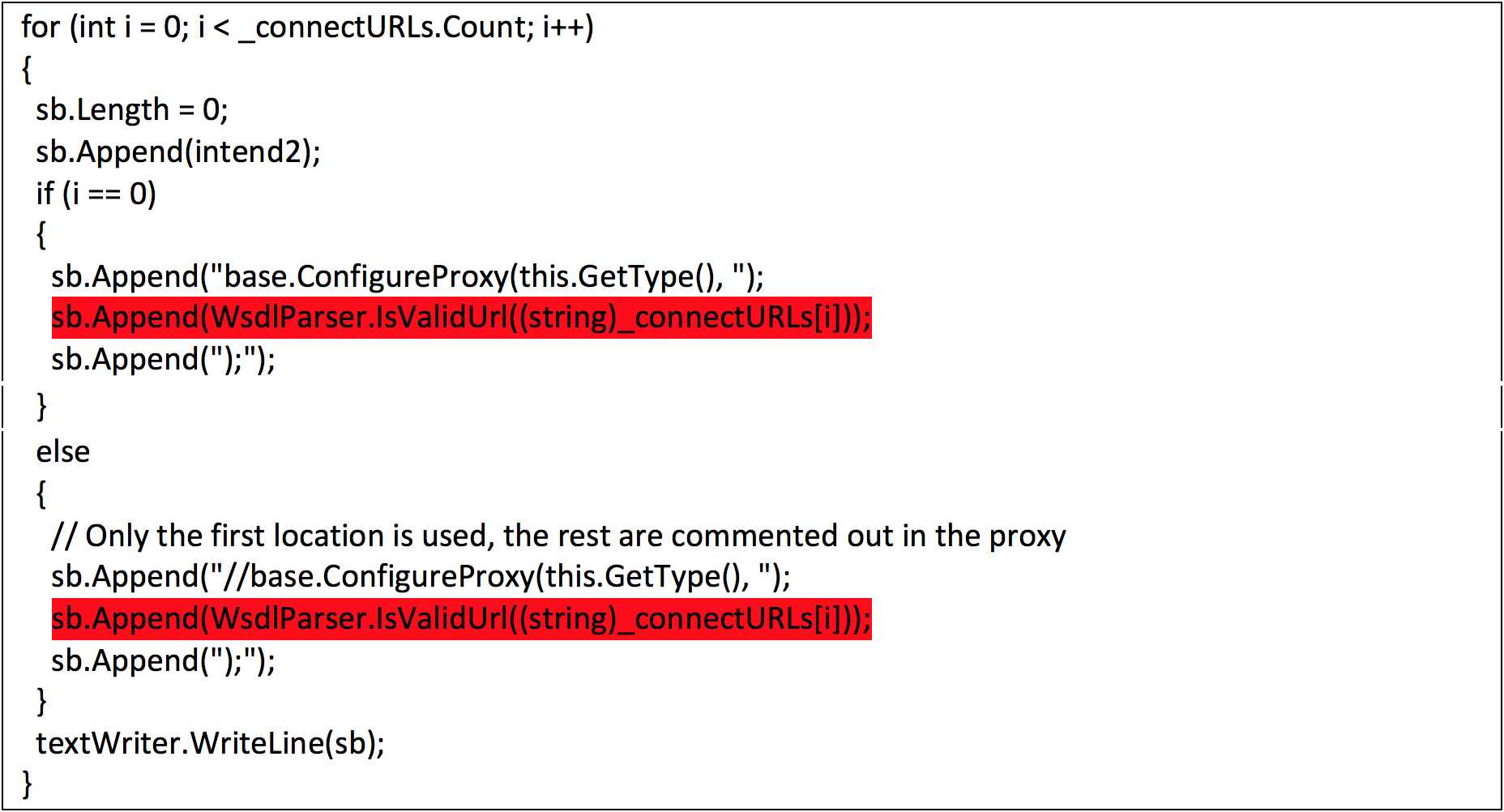
FireEye Uncovers CVE-2017-8759: Zero-Day Used in the Wild to Distr - exploit database
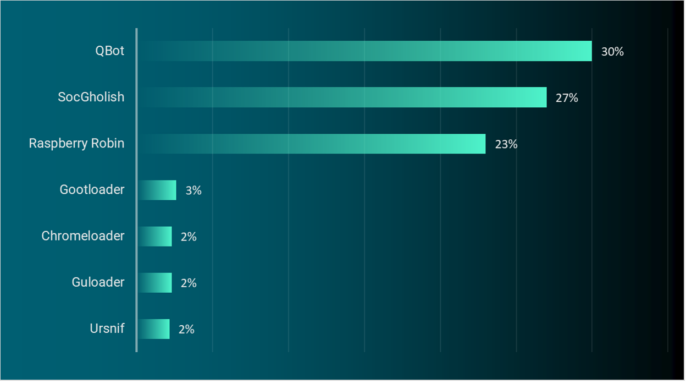
3 Malware Loaders You Can't (Shouldn't) Ignore - ReliaQuest
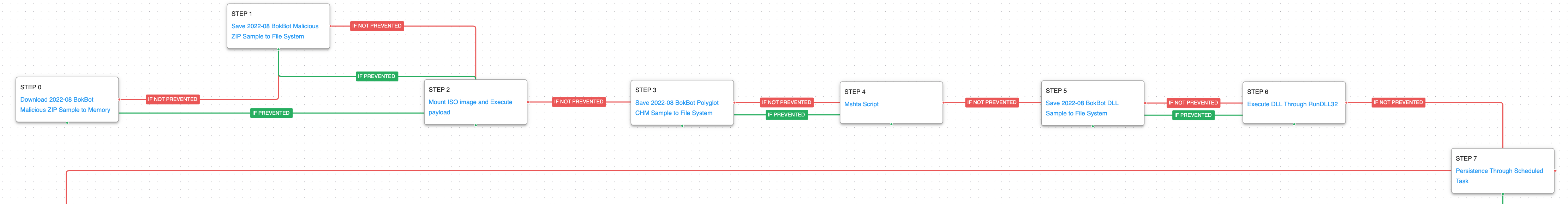
Emulating the Infamous Modular Banking Trojan BokBot - AttackIQ

Swedish Windows Security User Group » ransomware

AgentTesla Information-Stealing Malware Delivered in Cyber-Attacks on Ukrainian Government Entities - SOC Prime
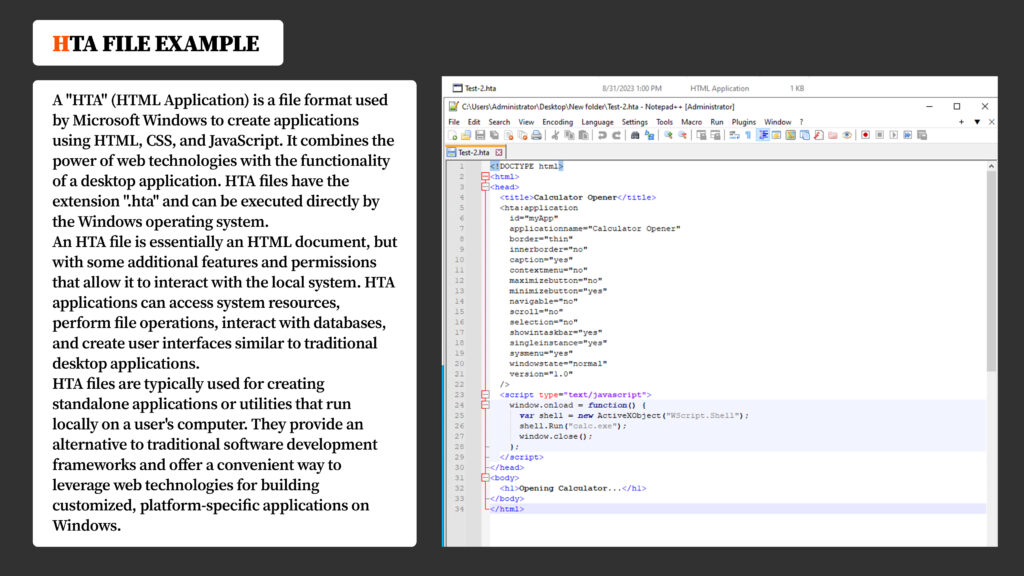
System Binary Proxy Execution Rundll32, Nordic Defender
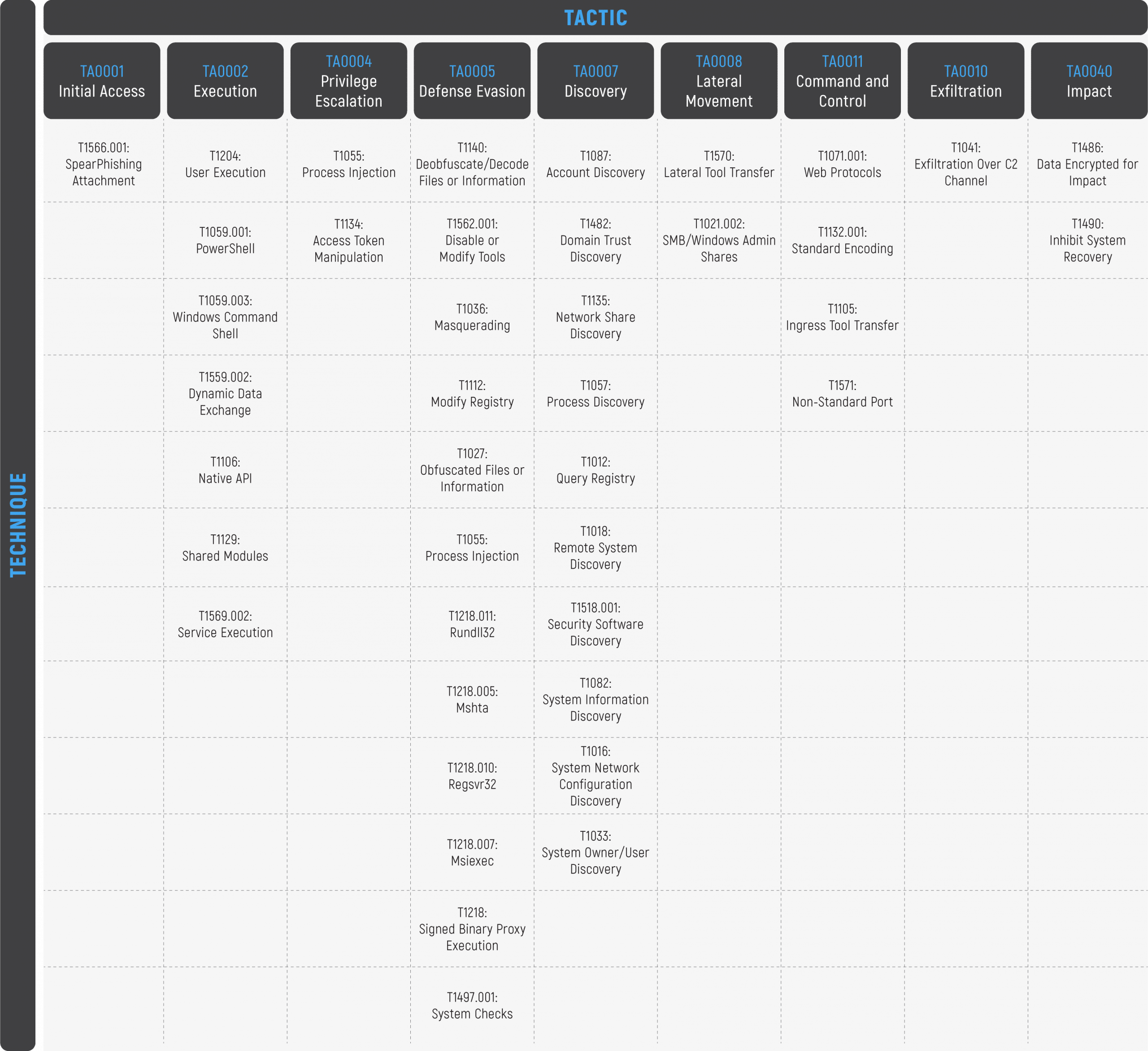
Shelob Moonlight – Spinning a Larger Web From IcedID to CONTI, a Trojan and Ransomware collaboration - Cynet
Rundll32: The Infamous Proxy for Executing Malicious Code

Microsoft experts linked Raspberry Robin malware to Evil Corp
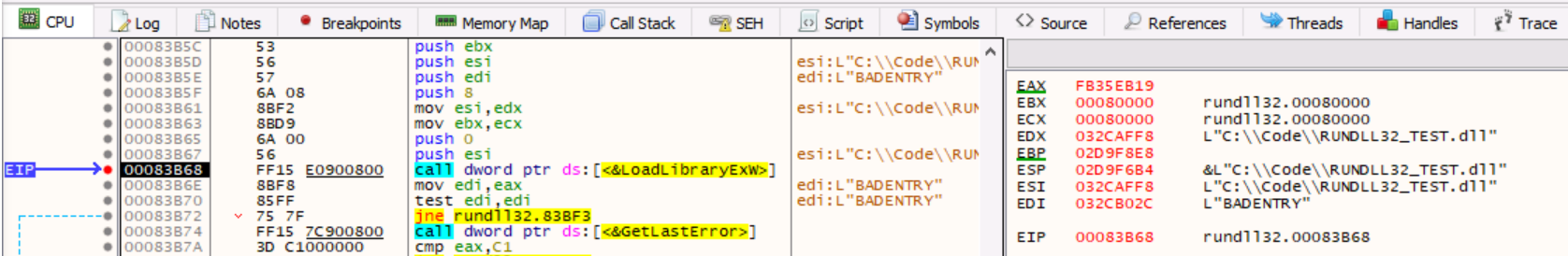
Rundll32: The Infamous Proxy for Executing Malicious Code
de
por adulto (o preço varia de acordo com o tamanho do grupo)


/cloudfront-us-east-1.images.arcpublishing.com/pmn/7DEXZMWLPNEZLAUL7W36FG6DBQ.jpg)

