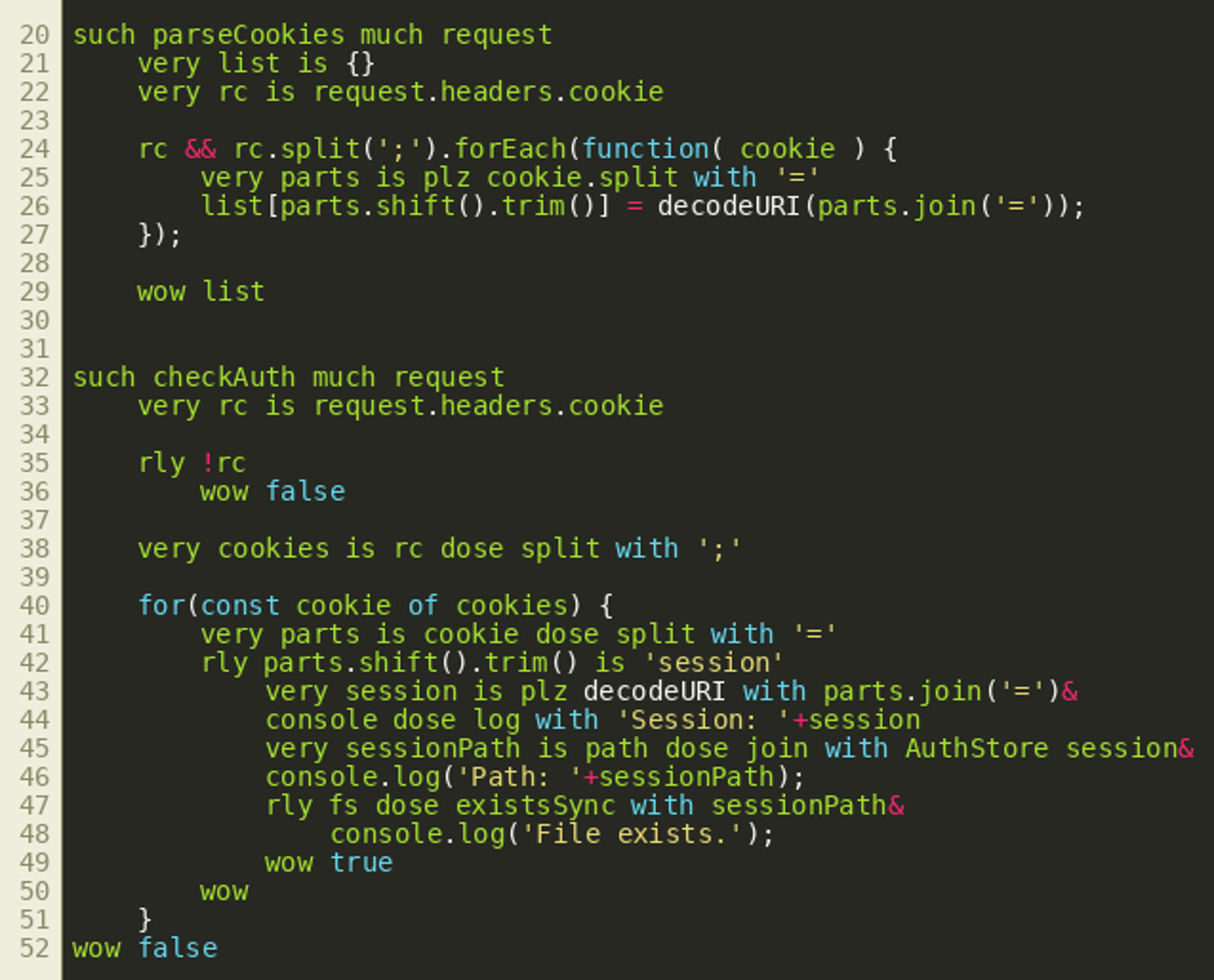
Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike

PROUD-MAL: static analysis-based progressive framework for deep

Detail procedure of malware analysis

Malware Analysis: Steps & Examples - CrowdStrike

Malware Analysis: Protecting Your Network from Cyber Attacks
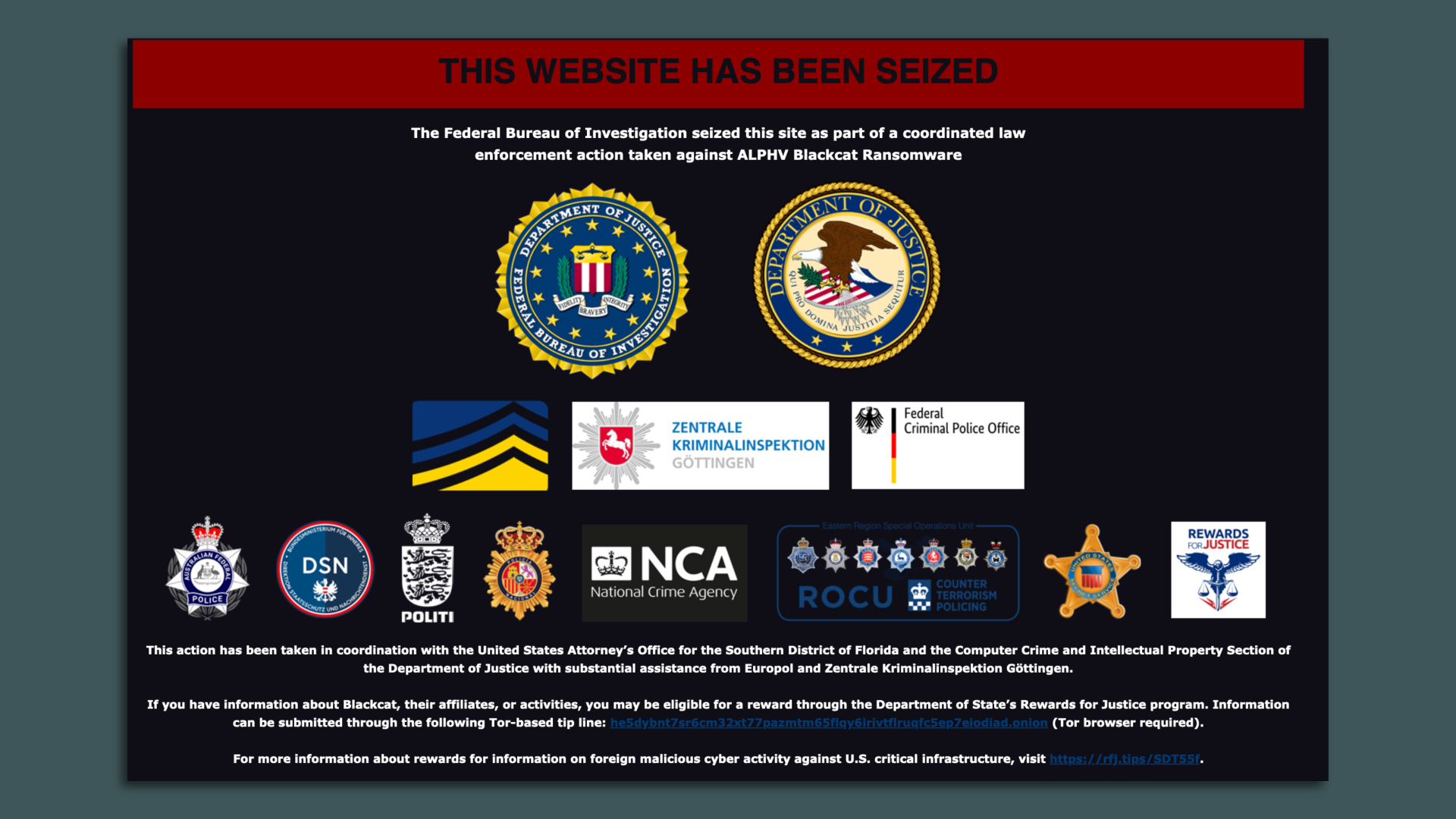
U.S. law enforcement seizes BlackCat ransomware site, distributes

AlienVault - Open Threat Exchange

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

Robust Malware Detection Models: Learning From Adversarial Attacks

Malware analysis Program_Install_and_Uninstall Malicious activity
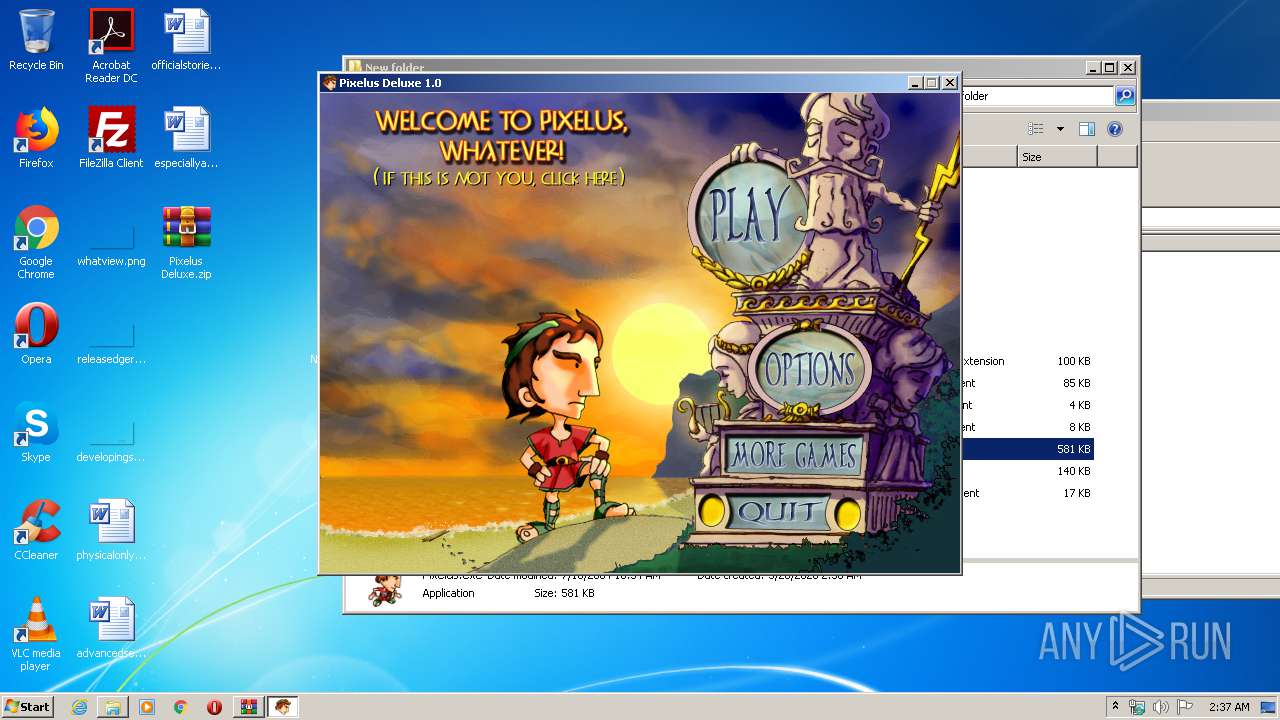
Malware analysis Pixelus Deluxe.zip Malicious activity
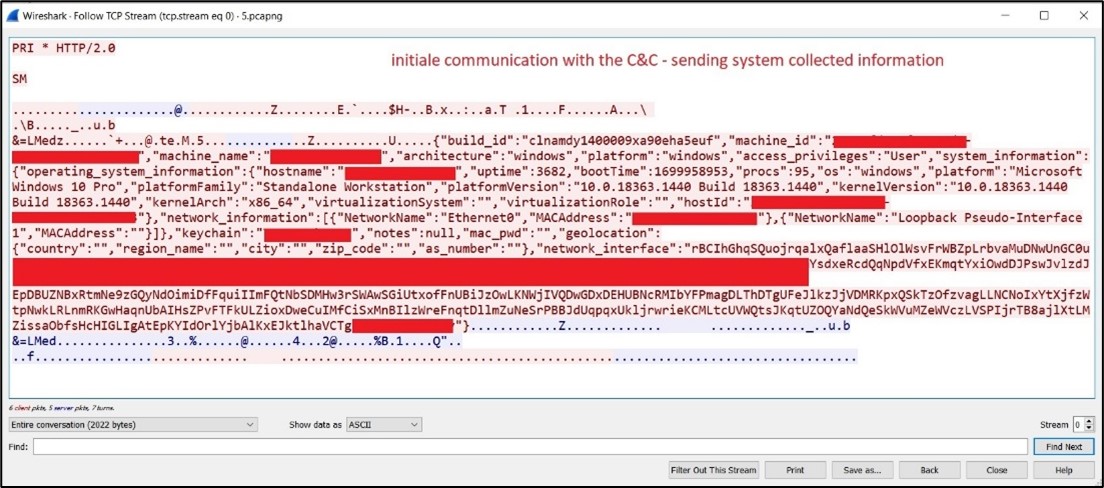
Behind the Scenes: JaskaGO's Coordinated Strike on macOS and Windows

Intro to Malware Analysis: What It Is & How It Works - InfoSec
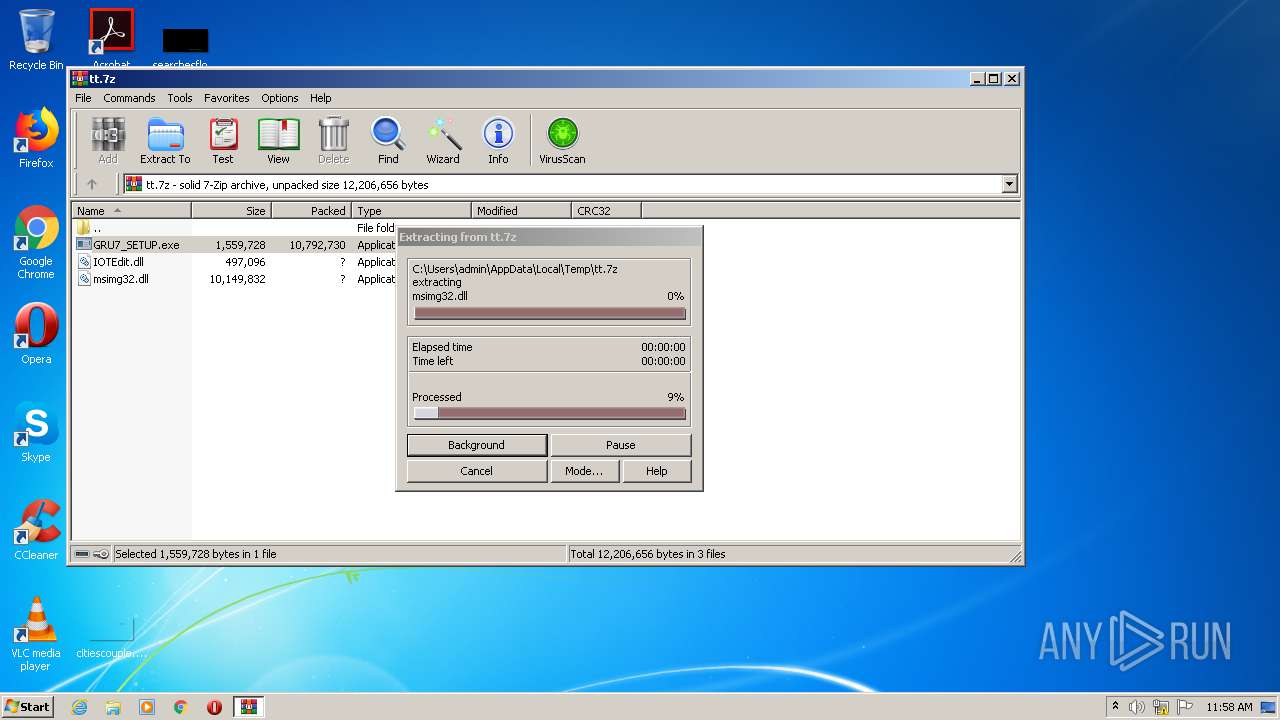
Malware analysis tt.7z Malicious activity
de
por adulto (o preço varia de acordo com o tamanho do grupo)