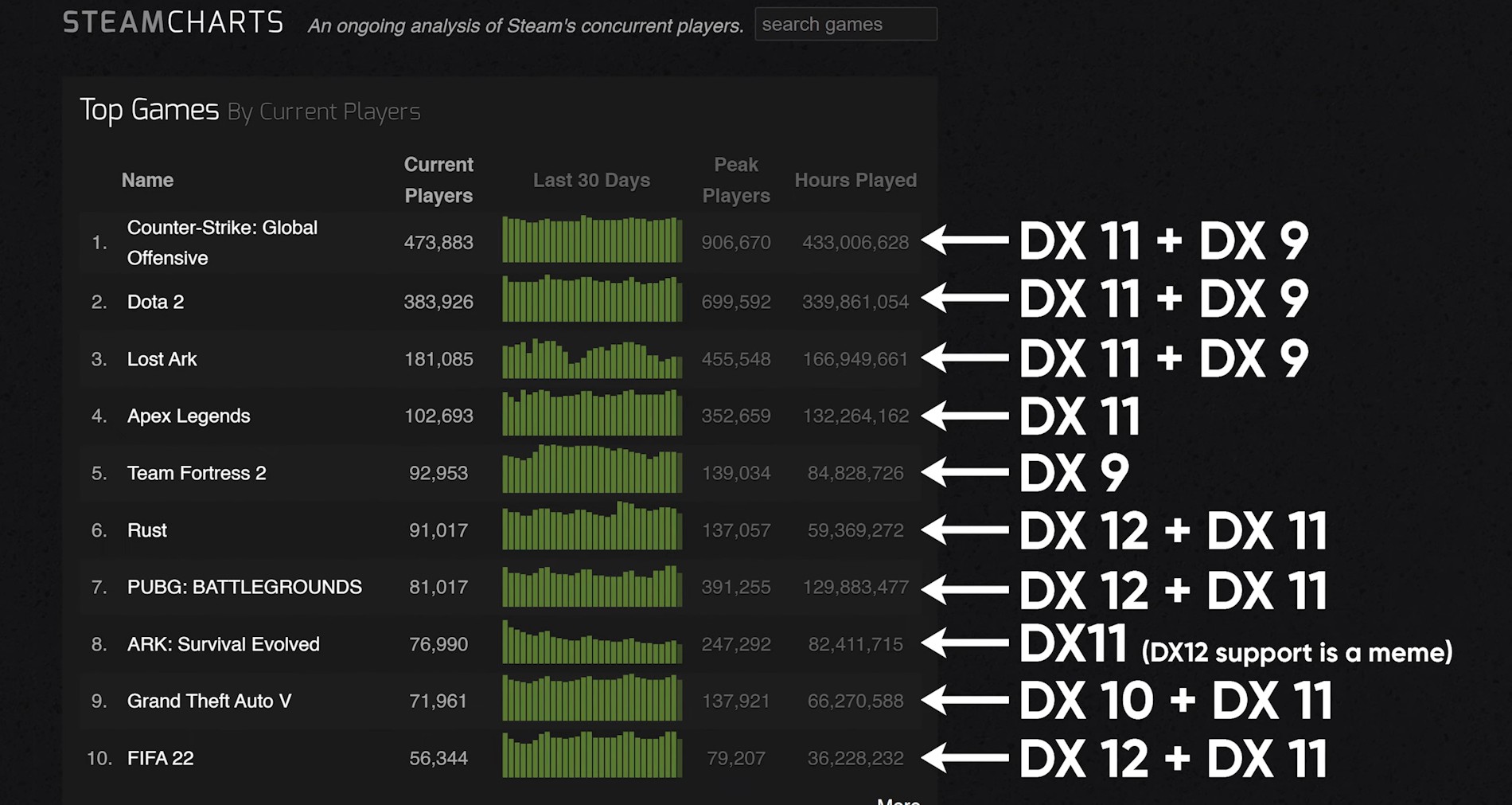
Inside ImageTragick: The Real Payloads Being Used to Hack Websites
Por um escritor misterioso
Descrição
Get the latest news on how products at Cloudflare are built, technologies used, and join the teams helping to build a better Internet.
Cracking the lens: targeting HTTP's hidden attack-surface

Hacker found a way to hack Facebook by exploiting the ImageMagick flaw

S. Rohit on LinkedIn: #bugbounty #bugbountytips #bugbountytip #cybersecurity #ethicalhacking…

How I abused the file upload function to get a high severity vulnerability in Bug Bounty, by Omar Hashem
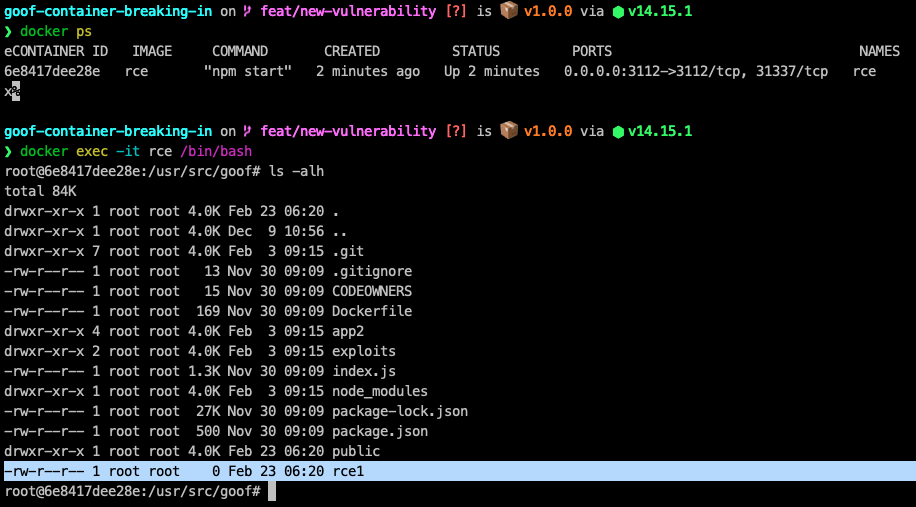
How I was hacking docker containers by exploiting ImageMagick vulnerabilities

Inside ImageTragick: The Real Payloads Being Used to Hack Websites
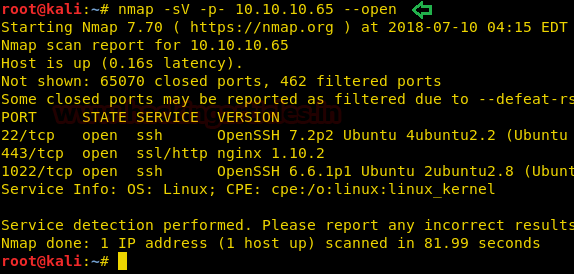
Hack the Box Challenge: Ariekei Walkthrough - Hacking Articles

Hack the Box Challenge: Ariekei Walkthrough - Hacking Articles
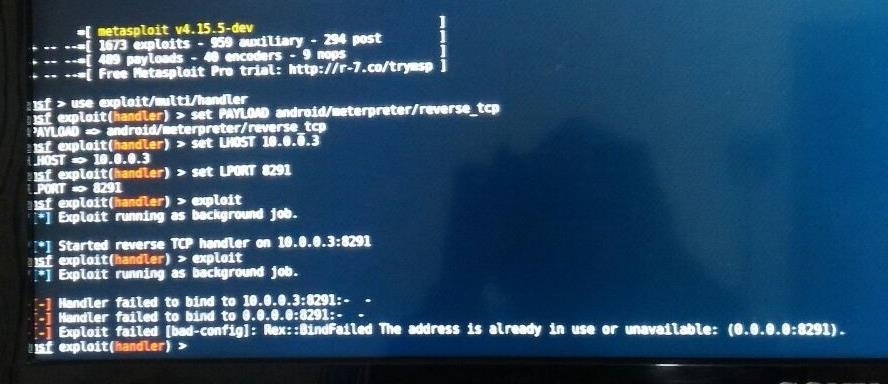
Exploit Failed [Bad-Config] Rex::Bindfailed « Null Byte :: WonderHowTo

ImageTragick and Rails - Speaker Deck

OS Command Injection, Learn AppSec
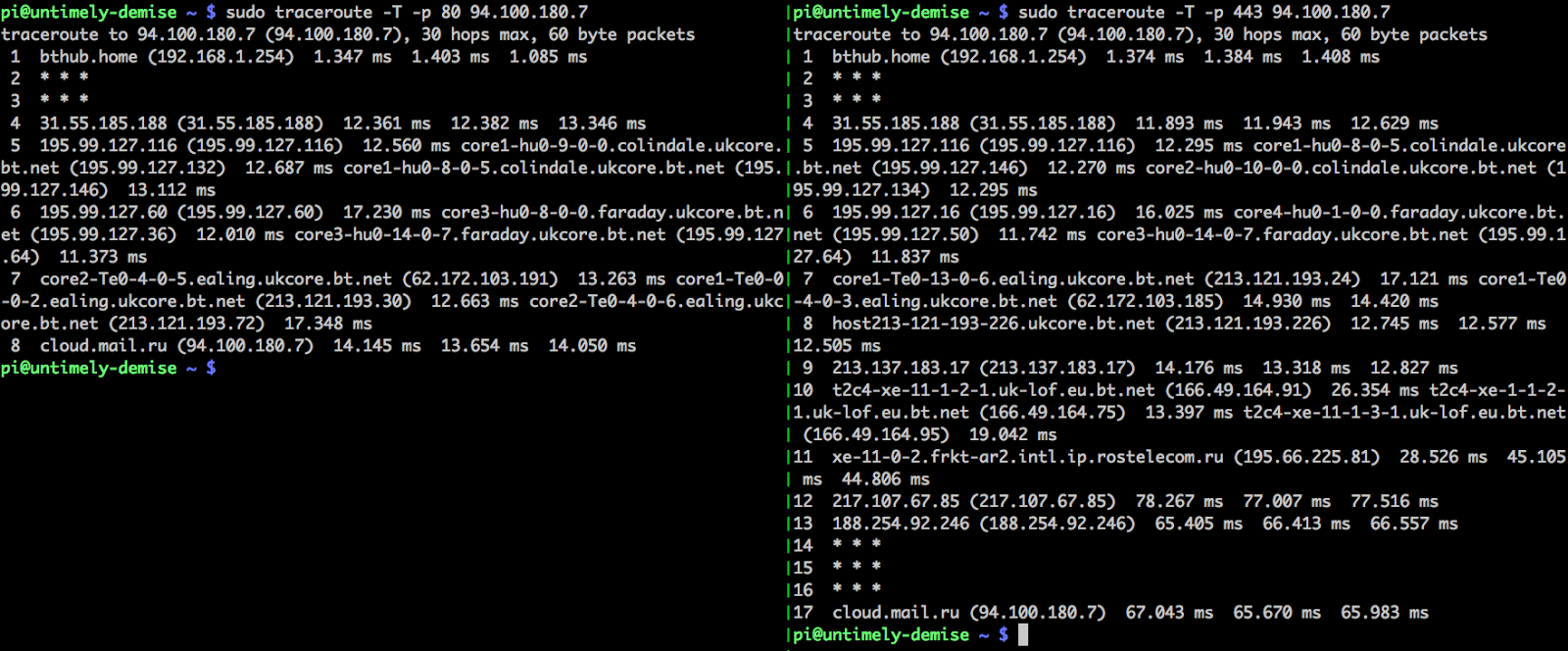
Cracking the lens: targeting HTTP's hidden attack-surface
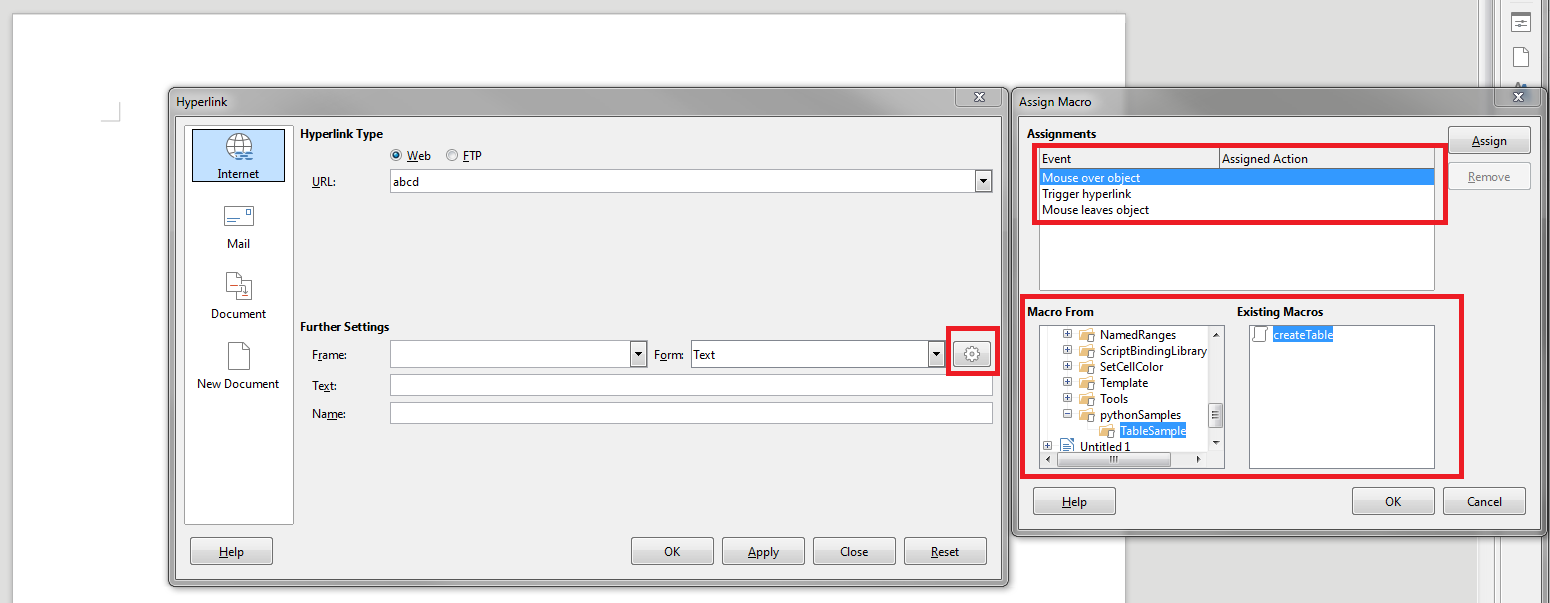
InsertScript

Warning — Widely Popular ImageMagick Tool Vulnerable to Remo - vulnerability database

Stop Container Escape and Prevent Privilege Escalation
de
por adulto (o preço varia de acordo com o tamanho do grupo)