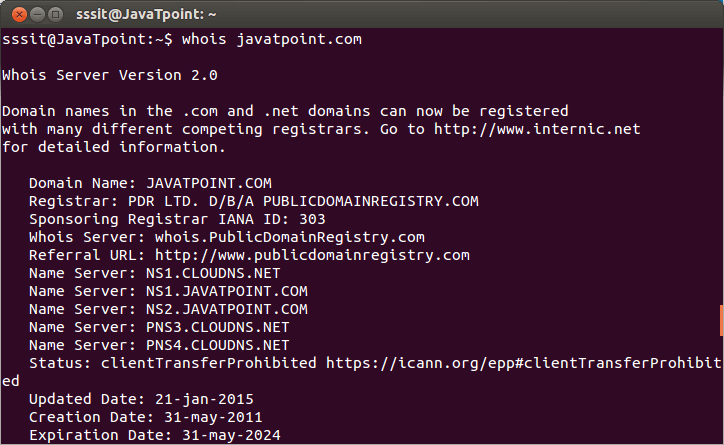
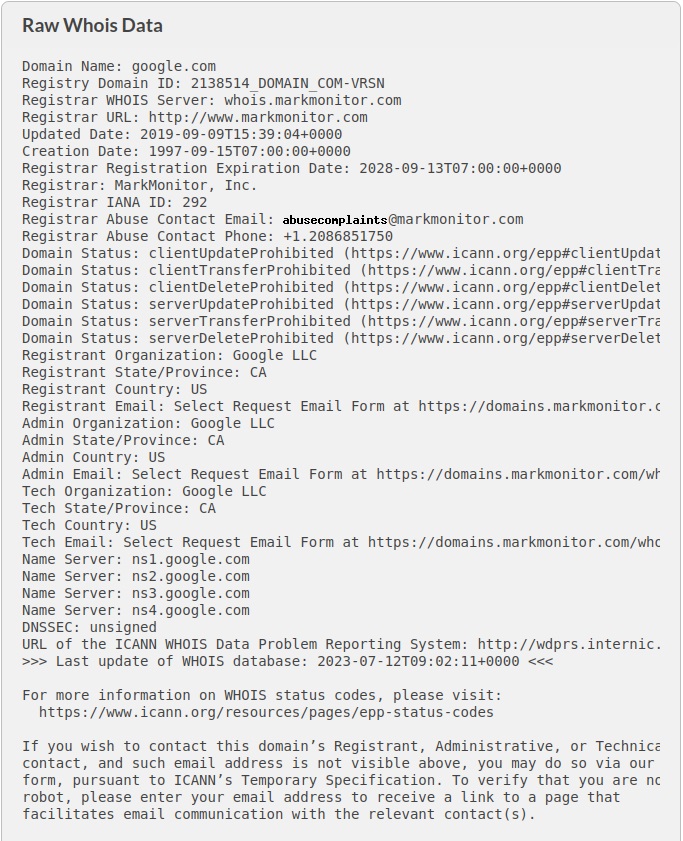
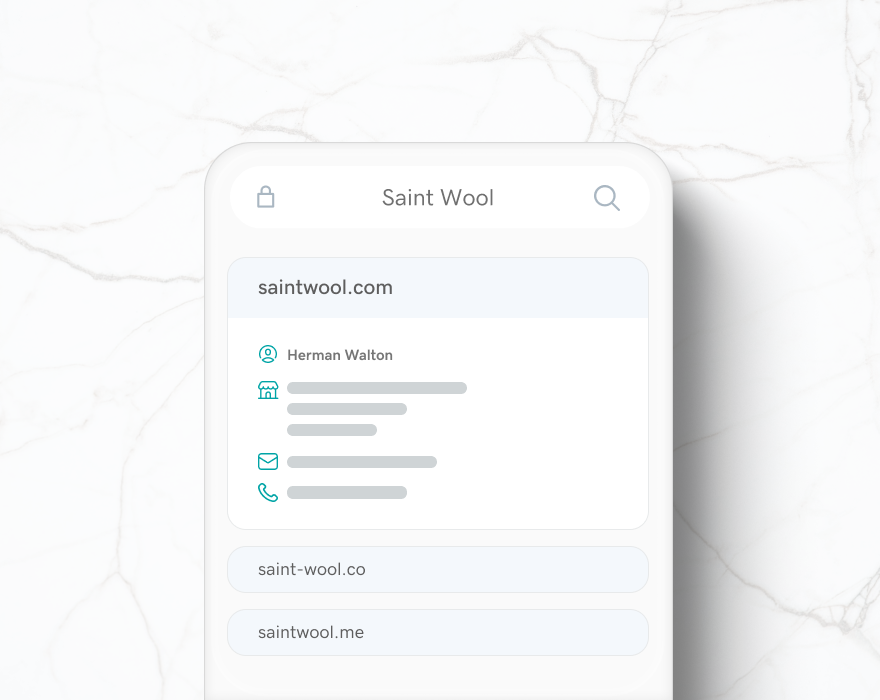
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Descrição
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

7 powerful pentesting tools (& why you should stop pedestalizing them)

Killnet Claim They've Stolen Employee Data from Lockheed Martin

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)
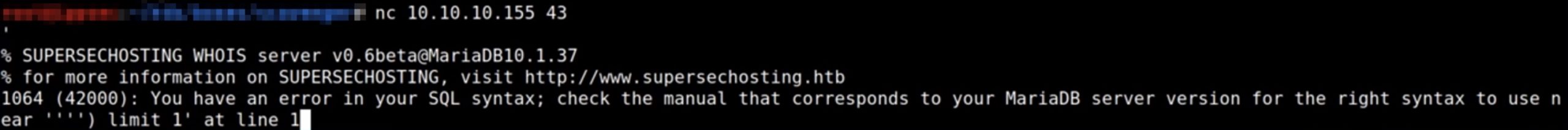
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Infrastructure Hacking: WHOIS Protocol » Hacking Lethani

Linux Challenges - Cyber Security / Ethical Hacking

DNC Hacks: How Spear Phishing Emails Were Used

Should you use Let's Encrypt for internal hostnames? – Terence Eden's Blog

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

2600: The Hacker Quarterly (Volume 5, Number 1, Spring 1988), PDF, Broadcasting

Infrastructure Hacking: Telnet Protocol » Hacking Lethani
de
por adulto (o preço varia de acordo com o tamanho do grupo)