Detecting Linux Anti-Forensics: Timestomping
Por um escritor misterioso
Descrição
#160; Threat actors can modify the timestamps on malicious files to evade detection. This technique has been used time and time again across va
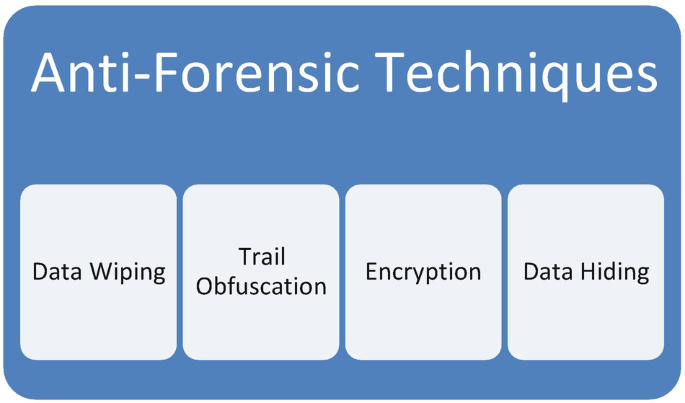
Anti-forensics

Anti-Forensic: Swipe Footprint with Timestomp - Hacking Articles

Anti-forensics in ext4: On secrecy and usability of timestamp

Anti-Forensic: Swipe Footprint with Timestomp - Hacking Articles
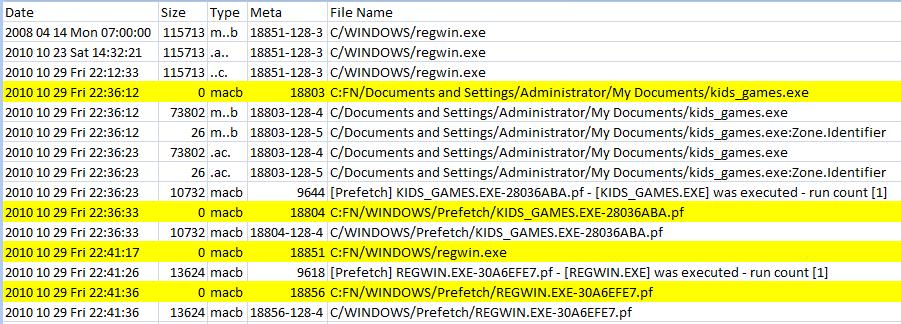
SANS Digital Forensics and Incident Response Blog

Anti-forensics Securing Network Infrastructure

PDF) Three Anti-Forensics Techniques that pose the Greatest Risks
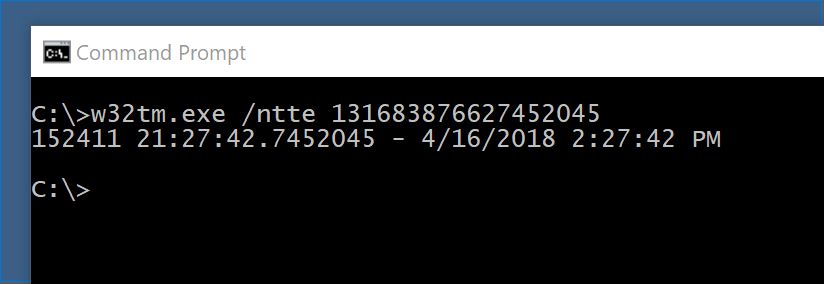
Using osquery for remote forensics
Anti-Forensic Techniques Used By Lazarus Group - ASEC BLOG

Lina L. en LinkedIn: Detecting Linux Anti-Forensics: Timestomping
de
por adulto (o preço varia de acordo com o tamanho do grupo)